| Lesson 6 | Domains |
| Objective | Define the function and purposes of Windows domains. |
Windows Domain Controller
As you know, the core unit of the logical structure in Active Directory is the domain. The domain serves many functions: It can act as a security boundary and as a unit of replication. Windows domains, with which you may be familiar, are also security boundaries but function very differently from Windows 2000 Active Directory domains.
- Domain as Security Boundary A domain administrator has the permissions and rights to administer within that domain only, unless the administrator is explicitly granted those rights in another domain. Furthermore, administrative authority can be granted over one or a group of organizational units within a domain, providing for much more granular administration. By contrast, in Windows NT, the domain was the smallest administrative unit, so you could not grant administrative authority to a user for part of a domain.
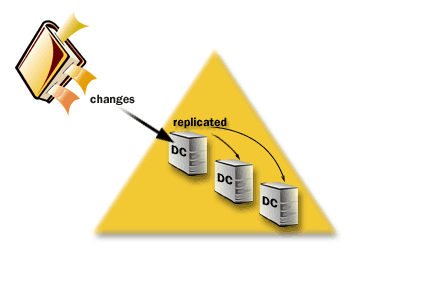
- Domain as unit of Replication: All domain controllers in a domain participate in replication and contain a complete copy of all directory information for their domain.
How a Domain behaves in Mixed Mode
In Active Directory, a domain that is operating in "Mixed Mode" refers to a compatibility mode that allows the domain to support both Windows NT 4.0-based and Active Directory-based domain controllers. This mode is relevant when transitioning from an older network operating system environment to a more modern Active Directory environment, allowing for backward compatibility with older software and systems.
Here are the key characteristics of Mixed Mode in Active Directory:
Upgrading from Mixed Mode to a higher domain functional level is a critical step in leveraging the full capabilities of Active Directory and improving the security and efficiency of network management.
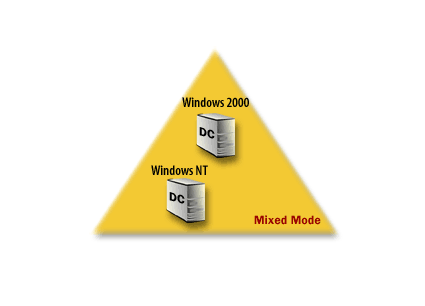
Once established, a domain can function as a mixed-mode[1] or native-mode[2] domain. What does this mean?
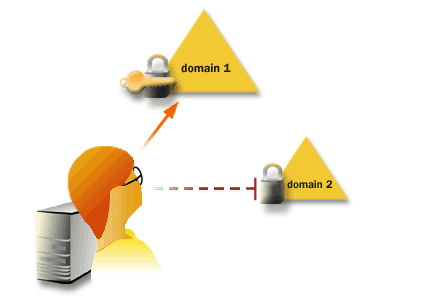
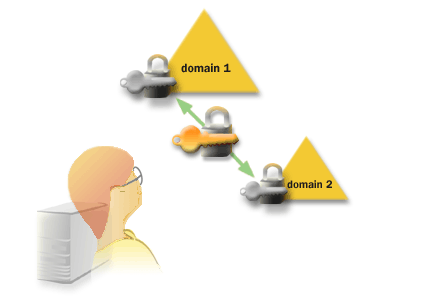
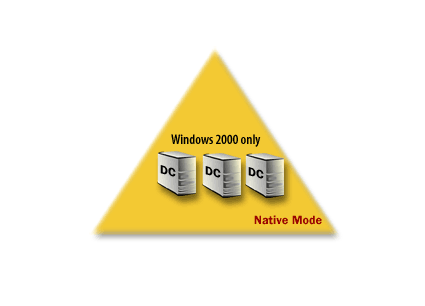
A mixed-mode domain supports domain controllers that are running either Windows 2000 or Microsoft Windows NT. In a native-mode domain, all domain controllers run Windows 2000. After you install Active Directory and establish a domain, the domain and Active Directory are running in mixed-mode until you explicitly change it to native-mode. The series of images below elaborates on these domain definitions and shows how the domain functions once it has been created.
Here are the key characteristics of Mixed Mode in Active Directory:
- Support for NT 4.0 Domain Controllers: Mixed Mode allows Windows NT 4.0 domain controllers to coexist with newer Active Directory domain controllers. This is crucial during a migration phase where an organization is moving to Active Directory but still operates some legacy systems that depend on the older NT 4.0 domain controllers.
- Domain Functional Level: The concept of domain functional levels provides a way to specify the versions of Windows Server domain controllers that you can run within a domain. In Mixed Mode, the domain operates at a lower functional level, typically at the level of Windows 2000, to ensure compatibility with NT 4.0 domain controllers.
- Group and User Management: In Mixed Mode, group and user management still adheres to limitations that were present in NT 4.0. For example, you are limited to using security groups in the manner they were used in NT 4.0, without the benefits of newer features like nested groups.
- Transition to Native Mode: Once all domain controllers are upgraded to Active Directory and no longer require compatibility with NT 4.0, the domain can (and should) be switched from Mixed Mode to Native Mode. Native Mode unlocks newer Active Directory features, such as universal groups, nested group memberships, group conversion (converting between security and distribution groups), and advanced delegation of administration, which are not available in Mixed Mode.
- Security and Functionality: Mixed Mode is less secure and offers fewer features than Native Mode. The presence of NT 4.0 domain controllers inherently limits the ability to use more robust security protocols and enhancements that are available in newer versions of Windows Server.
- Deprecated Status: It's important to note that Mixed Mode is a deprecated feature in newer versions of Active Directory and Windows Server, as support for Windows NT 4.0 has been phased out. Organizations are encouraged to update all systems to be compatible with at least Windows Server 2003 or higher, which allows the domain to operate in at least Windows 2000 Native Mode or higher.
Upgrading from Mixed Mode to a higher domain functional level is a critical step in leveraging the full capabilities of Active Directory and improving the security and efficiency of network management.
Once established, a domain can function as a mixed-mode[1] or native-mode[2] domain. What does this mean?
A mixed-mode domain supports domain controllers that are running either Windows 2000 or Microsoft Windows NT. In a native-mode domain, all domain controllers run Windows 2000. After you install Active Directory and establish a domain, the domain and Active Directory are running in mixed-mode until you explicitly change it to native-mode. The series of images below elaborates on these domain definitions and shows how the domain functions once it has been created.
Active Directory Domain Functions
Active Directory (AD) is a directory service developed by Microsoft for Windows domain networks. It provides a variety of network services and plays an integral role in the administration and security of Windows-based network environments. Among the many features offered by AD, domain functions and security boundaries are particularly important. Domain functions in Active Directory refer to the functional levels of Active Directory Domain Services (AD DS). These functional levels determine the available capabilities of the domain or forest, including advanced features that were introduced in newer versions of Windows Server. By raising the domain or forest functional level, organizations can utilize these enhanced features, which can include things like improved replication, finer-grained password policies, and additional Active Directory object types. It's important to note that once a domain or forest functional level is raised, it cannot be lowered without restoring from a backup. Furthermore, raising the functional level can restrict which versions of Windows Server can be used as domain controllers, as older versions may not support the newer features.
- Security Boundaries:
In Active Directory, a security boundary is defined as a construct or container where a certain security policy, or set of policies, can be enforced and cannot be overridden. The primary security boundary in Active Directory is the forest. A forest is a collection of one or more AD domains that share a common schema, configuration, and global catalog, and are linked with two-way transitive trust relationships. Since the forest represents the security boundary, objects such as users, computers, and groups cannot access resources in another forest unless explicit trust relationships are established. Domains within the forest do not serve as security boundaries, but administrative boundaries. While domains can be managed independently with their own policies and administrators, these configurations can technically be overridden by administrators with forest-level permissions. It's crucial to properly design and manage your Active Directory structure, taking into account these aspects of domain functions and security boundaries. This will help ensure a secure and efficient network environment.
Deploying Active Directory
Structure and Storage Technologies
Domains can be structured in a forest to provide data and service autonomy and to optimize replication with a given region.
This separation of logical and physical structures improves manageability and reduces administrative costs because the logical structure is not affected by changes in the physical structure. The logical structure also makes it possible to control access to data. This means that you can use the logical structure to compartmentalize data so that you can control access to it by controlling access to the various compartments.
The data that is stored in Active Directory can come from many diverse sources. With so many different data sources and so many different types of data, Active Directory must employ some type of standardized storage mechanism so that it can maintain the integrity of the data that it stores. In Active Directory, objects are used to store information in the directory, and all objects are defined in the schema. The object definitions contain information, such as data type and syntax, that the directory uses to ensure that the stored data is valid. No data can be stored in the directory unless the objects that are used to store the data are first defined in the schema. The default schema contains all the object definitions that Active Directory needs to function. However, you can also add object definitions to the schema. While the directory is exposed to you through a logical structure that consists of elements such as domains and forests, the directory itself is implemented through a physical structure that consists of a database that is stored on all domain controllers in a forest. The Active Directory data store handles all access to the database. The data store consists of both services and physical files. These services and physical files make the directory available, and they manage the processes of reading and writing the data inside the database that exists on the hard disk of each domain controller.
The change from mixed-mode to native-mode is a one-way process; you cannot change from native-mode to mixed-mode.
In the next lesson, you will learn more about organizational units.
The data that is stored in Active Directory can come from many diverse sources. With so many different data sources and so many different types of data, Active Directory must employ some type of standardized storage mechanism so that it can maintain the integrity of the data that it stores. In Active Directory, objects are used to store information in the directory, and all objects are defined in the schema. The object definitions contain information, such as data type and syntax, that the directory uses to ensure that the stored data is valid. No data can be stored in the directory unless the objects that are used to store the data are first defined in the schema. The default schema contains all the object definitions that Active Directory needs to function. However, you can also add object definitions to the schema. While the directory is exposed to you through a logical structure that consists of elements such as domains and forests, the directory itself is implemented through a physical structure that consists of a database that is stored on all domain controllers in a forest. The Active Directory data store handles all access to the database. The data store consists of both services and physical files. These services and physical files make the directory available, and they manage the processes of reading and writing the data inside the database that exists on the hard disk of each domain controller.
The change from mixed-mode to native-mode is a one-way process; you cannot change from native-mode to mixed-mode.
In the next lesson, you will learn more about organizational units.
[1]Mixed-mode domain: You should apply it only to systems that have had the Exchange Server Analyzer Tool run against them and are experiencing that specific issue. The Exchange Server Analyzer Tool, available as a free download, remotely collects configuration data from each server in the topology and automatically analyzes the data. The resulting report details important configuration issues, potential problems, and nondefault product settings. By following these recommendations, you can achieve better performance, scalability, reliability, and uptime.
[2]Native-mode domain: A domain in which all domain controllers are running Windows 2000 (no "down-level" - domain controllers).