| Lesson 4 | Examining system logs |
| Objective | Examine Contents of System Logs for Significant Events. |
Examine Contents of System Logs for Significant Events
Before you begin looking through logfiles for significant events, you must know and understanding the format of the logfiles. Most Linux logfiles have a common, fixed format that has four elements
- The date and time of the message
- The hostname from where the message came, which is important when you have enabled centralized system logging
- The name of the application or subsystem from where the message came--for example,
kernel,ftpd, and so on - The actual message,>which is the remainder of the line following the colon
The following diagramshows typical entries from a
/var/log/messages logfile.
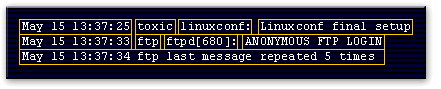
toxicThe message's originating host
linuxconf:The name of the application or subsystem
linuxconf final setupThe log message
May 15 13:37:33The date and time of the message
ftp:The message's originating host
ftpd[680]:The application's or subsystem's name and process ID.
ANONYMOUS FTP LOGINThe log message
May 15 13:37:34 ftp last message repeated 5 timesThe Linux system logger tries to limit the number of repeated messages. Consequently, it will condense repeated log messages into a single entry that states how many times the last message repeated. In this example, the anonymous ftp login entry was logged six times, but only the first time and the system message of five repeats were actually logged.
Log Message
The xferlog logfile has its own format. Check the xferlog man page for a description of each field.
Looking for significant events
Examining the system logs is an important part of system administration. To ensure that problems are caught and resolved in a timely fashion, you should check your system's logs for significant events.
If you have built a monolithic kernel for your firewall (strongly suggested), check for module insertion activity with grep insmod /var/log/messages. A monolithic kernel should not have any modules inserted into it; if someone tried, it might be a sign of security compromise. View the table below to see how to identify commonly logged, significant events.
If you have built a monolithic kernel for your firewall (strongly suggested), check for module insertion activity with grep insmod /var/log/messages. A monolithic kernel should not have any modules inserted into it; if someone tried, it might be a sign of security compromise. View the table below to see how to identify commonly logged, significant events.
Examining Root Logins
| Event | How to identify |
|---|---|
| root logins | grep "login.*for user root" /var/log/messages |
| root login failures | grep "FAILED LOGIN.*FOR root" /var/log/messages |
| su failures | grep "failure.*root for su" /var/log/messages |
| anonymous ftp | grep "ANONYMOUS" /var/log/messages |
| password updates | grep "password" /var/log/messages |
| general error strings | egrep -i "(fatal|unauthorized|illegal|denied|hack|sniff|spoof|spy)" /var/log/messages |
The next lesson explains how to configure the system log.