| Lesson 5 | Configuring the system log |
| Objective | Configure the System Log. |
Configuring System Log
To configure the Linux system logging facility, use the
A facility[1] and severity[2] combine to form a selector. Linux predefines valid facilities and severities, which applications use to log entries to the system logger. To make a selector, place the facility name followed by a period in front of the severity. For example, an email program might use the
/etc/syslog.conf file. This file enables you to specify how log messages will be handled when they arrive, such as what file or host will log them. Every line in this file is called a rule. Rules map selectors to actions, which allows the Linux system logging facility to route messages of certain types to different locations. For example, you might want to route debugging messages and critical messages to different locations.
A facility[1] and severity[2] combine to form a selector. Linux predefines valid facilities and severities, which applications use to log entries to the system logger. To make a selector, place the facility name followed by a period in front of the severity. For example, an email program might use the
mail.warn selector if it is unable to download your email.
Sending log messages to Different Locations
The system logger checks a log message's selector against selectors defined in
You can specify actions that
By default, emergency messages (those with a severity of
/etc/syslog.conf.
If the selector is configured in /etc/syslog.conf, the system logger performs the associated action.
You can specify actions that
- log the message to a file
- broadcast the message to all logged-in users
- write the message to the system console
- transmit the message to remote logging daemons across the network
By default, emergency messages (those with a severity of
emerg) are broadcast to all users, and most other messages are written to the standard system logfile /var/log/messages.
The following series of images discuss how to configure the /etc/syslog.conf file to log a selector to a particular logfile.
Configuring System Log
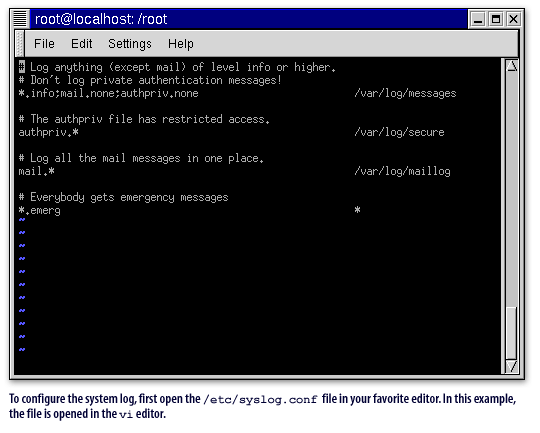
/etc/syslog.conffile in your favorite editor.
In this example, the file is opened in the
vi editor.
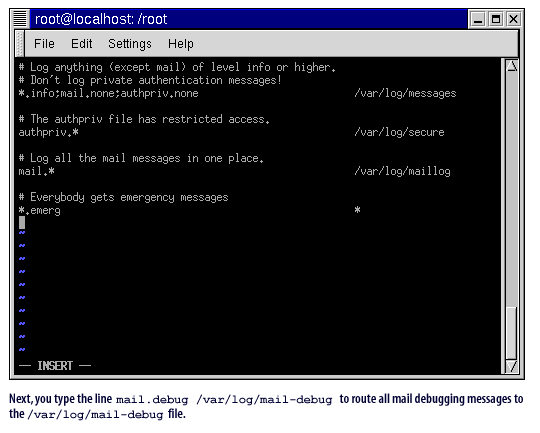
mail.debug /var/log/mail-debug
to route all mail debugging messages to the
/var/log/mail-debugfile.
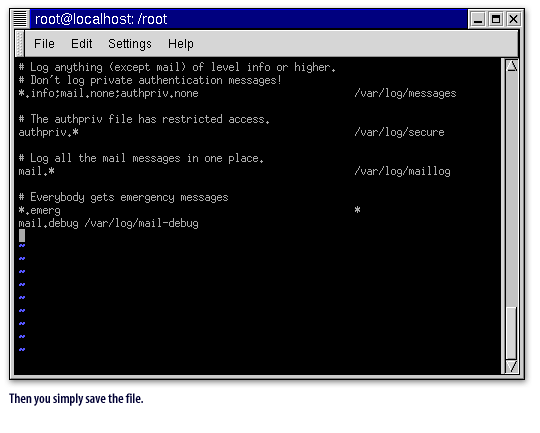
Sending Log messages to an Alphanumeric Pager
If you would like to be notified immediately of emergency messages, you can configure Linux to send them to your
alphanumeric pager.
You can configure your Linux system to send log messages to an alphanumeric pager. You probably only want severe messages sent to the pager, and you can configure this behavior through
Next, configure a
The /etc/syslog.conf file doesn't directly support sending email, so you need the cron job to mail the logfile.
/etc/syslog.conf and a cron script. First, decide which messages you want to send to the pager and give them a special logfile. The example below sends all critical kernel (kern.crit selector) messages and all emergency messages to the /var/log/emergency logfile.
kern.crit /var/log/emergency
*.emerg /var/log/emergency
Next, configure a
cron job to run every 20 seconds and check to see if /var/log/emergency exists.
If it does, mail the file's contents to the alphapager then delete the file.
The /etc/syslog.conf file doesn't directly support sending email, so you need the cron job to mail the logfile.
Using rsh for remote execution
While previous commands, such as rcp and ftp, can help you share files among computers on your network, rsh lets you share the processors.
With rsh, it is simple to ask that a command be run on any computer for which you have rhosts access. Likewise, you can have the command's output printed on your screen, directed to a local file, or directed to a remote file.
Here are four examples of the rsh command:
In the first example, the who command is run on the remote computer named spruce and the output appears on the local screen. The second example runs the tail -f command to display messages as they arrive in the /var/log/messages file on maple. (This is a good way to remotely monitor log files in one quick command line.) The next command runs the man command to output the rlogin man page and outputs the results to the /tmp/rlman file on the local system. In the final example, the uname -a command runs on fir, but by quoting the arrows, the output is sent to the /tmp/name file on the remote computer, rather than the local one.
For firewall machines, you should send all logs to an internal machine for safekeeping. If a cracker breaks in and deletes your logs, you will have a copy on another machine. To erase those, the cracker would have to break into that machine as well, which takes time. For example, to send a copy of every logged message to the
The asterisks (
More information on configuring system logging is available in the syslog.conf man page.
Here are four examples of the rsh command:
$ rsh spruce who $ rsh maple "tail -f /var/log/messages" $ rsh pine "man rlogin" >> /tmp/rlman $ rsh fir "uname -a" ">>" /tmp/name
In the first example, the who command is run on the remote computer named spruce and the output appears on the local screen. The second example runs the tail -f command to display messages as they arrive in the /var/log/messages file on maple. (This is a good way to remotely monitor log files in one quick command line.) The next command runs the man command to output the rlogin man page and outputs the results to the /tmp/rlman file on the local system. In the final example, the uname -a command runs on fir, but by quoting the arrows, the output is sent to the /tmp/name file on the remote computer, rather than the local one.
For firewall machines, you should send all logs to an internal machine for safekeeping. If a cracker breaks in and deletes your logs, you will have a copy on another machine. To erase those, the cracker would have to break into that machine as well, which takes time. For example, to send a copy of every logged message to the
backup.internal.net machine, include the following entry in /etc/syslog.conf:
*.* @backup.internal.net
The asterisks (
*) are wildcards and indicate that anything matches. The "at" sign (@) signals that the following name (backup.internal.net) is a remote host on which to log messages.
More information on configuring system logging is available in the syslog.conf man page.
Restarting System Logger
Once you have made configuration changes, restart the system logging facility with
The next lesson explains how to maintain logs.
/etc/rc.d/init.d/syslog restart.
The next lesson explains how to maintain logs.
Configuring System Log
Before moving on to the next lesson, click the link below to read about configuring a system log.
Configuring System Log
Configuring System Log
[1]
Facility: Facilities are simply programs that can be configured to send notices to the system log. Common facilities include user, kern, mail, daemon, auth, lpr, news, uucp, and cron.
[2]
Severity: The severity level indicates the importance of a given message. The severity levels listed from most importance to least important are: emerg, alert, crit, err, warning, notice, info, debug, and none.