| Lesson 6 | Network file synchronization, part 1 |
| Objective | Use rdist to synchronize files between the local host and a remote machine. |
Linux Sync Files
As a system administrator, you may find it useful to create and maintain an operable backup machine that contains all the files you use
regularly. Your and/or your end users may also want to keep their desktop and laptop machines synchronized.
Linux enables you to synchronize the filesystems of the local host and a remote machine. You can use the
ssh, the secure shell, is a utility that allows log in to a remote system using encrypted data transfer.
Linux enables you to synchronize the filesystems of the local host and a remote machine. You can use the
rdist and rsync commands to synchronize and transfer data. However, if security is a concern, using rsync with ssh is preferable.ssh, the secure shell, is a utility that allows log in to a remote system using encrypted data transfer.
Synchronization using rdist
Rdist is an older facility for synchronizing files.
The
rdist works by connecting to a machine over the network that trusts[1] the local machine and sending the filesystems across the wire that you instruct rdist to send. The remote host must be running an rdist server that handles the connection from the rdist client on the local machine.The
rdist client consults a configuration file[2] whenever it is invoked. The configuration file knows which files are to be mirrored as well as other information necessary to do the synchronization.
The filesystem on the remote host is updated to match the source filesystem's contents on the local host.
rdist security concerns
It is not trivial to secure
The MouseOver below illustrates the differences between a trusted and untrusted connection.
rdist.
The remote machine must trust the local machine, which opens it to
spoofing attacks .
Data flowing from the local machine to the remote machine is also available for packet sniffers or other forms of eavesdropping.The MouseOver below illustrates the differences between a trusted and untrusted connection.
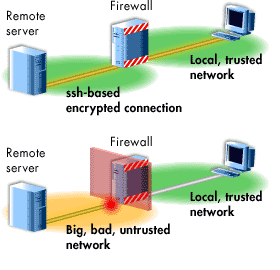
[1] Trust: Trust is a basic concept in security. The ability to trust means relying on the availability of another computer and the integrity of information provided by the other computer.
[2] Configuration file: A configuration file contains information such as settings or options to be used by a hardware device or program.