| Lesson 6 | Building a firewall (bastion host) |
| Objective | Build a firewall using a bastion host. |
Building three types of Firewalls
A bastion host can refer to any one of the three types of firewalls;
- packet filter,
- circuit-level gateway, or
- application-level gateway,
- Packet filter: A type of firewall devices that process network traffic on a packet-by-packet basis. Packet filter devices allow or block packets, and are typically implemented through standard routers.
- Circuit-level gateway: Circuit-level gateways are similar to packet filters. The main advantage of circuit-level gateways is their ability to provide network address translation.
- Application-level gateway: Application gateways function at all four layers of the TCP/IP suite. They are typically implemented through software installed on a specialized server. Application gateways are sometimes known as proxy servers.
Firewall components
Build your bastion host with the fewest possible components, both hardware and software, and do not install application services, such as Web servers. To prevent access to your internal network, design several levels of firewall devices. Do not rely on a single firewall device to protect your network. If your security is compromised, your security policy should state what to do.
Singled-homed bastion host
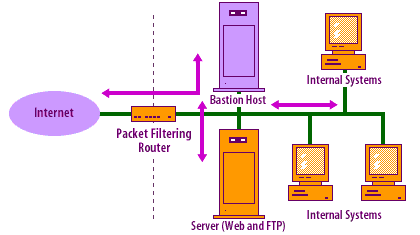
A singled-homed bastion host has only one network interface and is normally used for application-level gateway firewalls. The external router is configured to send all incoming data to the bastion host, and all internal clients are configured to send all outgoing data to the
host. Unfortunately, the router can be reconfigured to completely bypass the bastion host.
Dual-homed bastion host
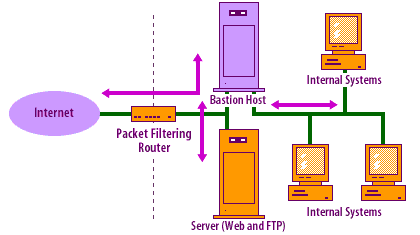
Dual-homed bastion hosts serve as application gateways, packet filters, and circuit gateways creating a complete break between the external network and internal network.
Securing bastion host
Secure your bastion hosts by:- Removing any unnecessary service, daemon, or application
- Removing IP routing to route the incoming and outgoing traffic to the firewall component
- Securing each bastion host individually and at every level
- Removing services rather than simply disabling them
Read the paragraph below to learn about single-purpose and internal bastion hosts.
1) single-purpose, 2) internal Bastion hosts
A separate bastion host dedicated to a single application is called a single-purpose bastion host. By using this type of bastion host, you do not jeopardize your security configuration and can implement strict security mechanisms such as authentication.
Internal bastion hosts reside inside the internal network and are normally used as application gateways that receive all incoming traffic from external bastion hosts. These provide an additional level of security in case the external firewall devices are compromised. All the internal network devices are configured to communicate only with the internal bastion host, and should not be affected by the compromised external bastion hosts.
Internal bastion hosts reside inside the internal network and are normally used as application gateways that receive all incoming traffic from external bastion hosts. These provide an additional level of security in case the external firewall devices are compromised. All the internal network devices are configured to communicate only with the internal bastion host, and should not be affected by the compromised external bastion hosts.