| Lesson 8 | TCP/IP packet construction |
| Objective | OSI model and how packets are sent across Internet. |
TCP-IP Packet Construction
We will now describe the OSI model and how packets are sent across the Internet. Information sent across the internet must be bundled into packets. The OSI model determines exactly how a network constructs packets to be sent across the Internet.
This model also determines which portions of the TCP/IP model match which level of the operating system.
What is packet sniffing during data transmission
Packet sniffing[1] is a process used to capture and analyze data packets as they are transmitted over a network. This is typically used for network troubleshooting, monitoring network traffic, analyzing performance issues, or for malicious purposes such as intercepting sensitive data. Here's how it typically works:
Due to these implications, the use of packet sniffers is often tightly controlled within an organization, and the protection of network data using encryption (like HTTPS) is strongly recommended to safeguard against unauthorized packet sniffing.
- Capture: Packet sniffing starts with the capture of packets. Network interfaces (like Ethernet, Wi-Fi) can be put into a "promiscuous mode" by the packet sniffer, which allows the interface to capture all packets that pass over the network, regardless of the destination address. This differs from the normal operation where the network device only picks packets addressed specifically to it.
- Analysis: Once packets are captured, they can be analyzed. The data within these packets can be decoded from raw binary to a more human-readable form using various tools or software like Wireshark. This analysis can provide insights into the types of traffic on the network, the volume, source, and destination of the packets, and potentially the content of the data being transmitted if the packets are not encrypted.
- Filtering and Logging: Sniffers can also filter packets to capture only those that meet certain criteria, such as packets from a specific IP address or those that use a specific protocol like HTTP or FTP. The relevant data can be logged for further analysis or auditing.
- Security Implications: While packet sniffing is a valuable tool for network administrators, it also poses security risks. Malicious packet sniffing can be used to intercept sensitive information like passwords, emails, and other private data if the data is not securely encrypted. It's a common technique in security breaches and spying activities.
Due to these implications, the use of packet sniffers is often tightly controlled within an organization, and the protection of network data using encryption (like HTTPS) is strongly recommended to safeguard against unauthorized packet sniffing.
Ad Guide to Network Security
- Routers: The fact that devices operate at different levels is especially important to remember when dealing with outers. A router is concerned only with directing packets from one computer to the appropriate location in a receiving computer. A router must understand the packet's structure only as far as the network layer is concerned.
- IP Datagrams: Because a router is restricted from other levels of the network, it is especially well suited for packet filtering. Packets are created using an encapsulation process, as shown in the following series of images below.
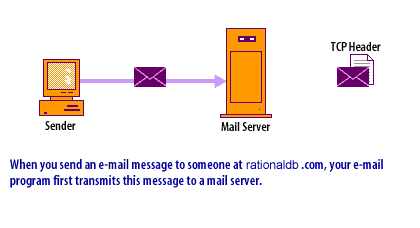
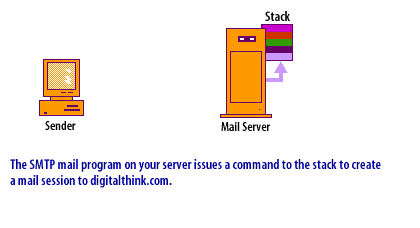
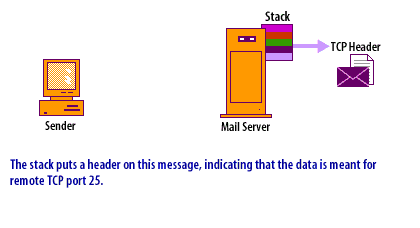
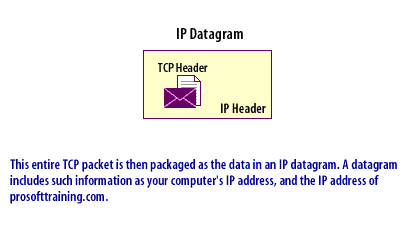
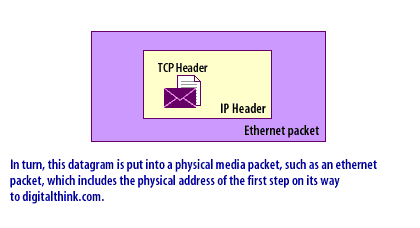
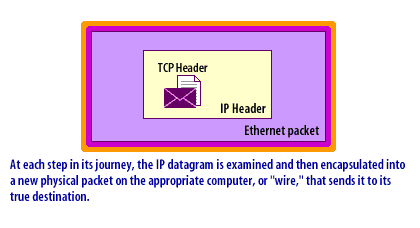
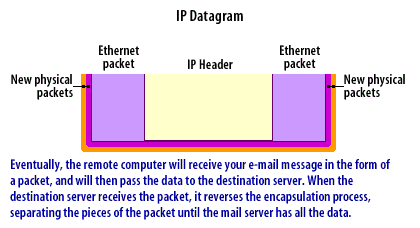
IP Datagrams
- data section: The program request or response becomes the data section for a TCP or UDP packet. This entire packet, including the header information, in turn, becomes the data portion of an IP packet. Controlling this process through routers and firewalls yields a high degree of security and is important to both firewalls and Virtual Private Networks[2].
- Hacker bypassing: The encapsulation process allows modification of specific layers of the TCP/IP protocol stack. For example, a hacker may route a virus through an unused router of your network directly bypassing a company's application gateways. The virus would reside in the stack's application layer and would not be detected by the router because the router looks only at the Internet layer.
Security for TCP/IP:
In order to best protect a network, security issues should be individually addressed for all layers of the TCP/IP protocol stack.
Addressing security issues at all layers of the TCP/IP protocol stack necessitates a holistic, multi-tiered approach. Each layer comes with its unique set of vulnerabilities and potential exploits, requiring specific strategies and tools. This discussion offers recommendations for each layer, starting from the bottom of the stack.
To summarize, securing the TCP/IP protocol stack is a complex task, requiring a multi-layered approach that addresses the unique challenges and vulnerabilities of each layer. It is not enough to focus on one layer at the expense of others; a single weak point can lead to a full-scale security breach. Therefore, security must be a comprehensive, end-to-end effort that considers the stack as a whole, supplemented by robust policies, procedures, and ongoing vigilance. Remember, in cybersecurity, prevention is always better than cure.
- Network Interface Layer: At the network interface layer, which is responsible for transferring data between the host and network, security measures should focus on preventing physical and direct data link attacks.
- Encryption: Encrypt all data at this layer to prevent eavesdropping, using protocols such as Wired Equivalent Privacy (WEP) or Wi-Fi Protected Access (WPA) for wireless connections. For wired connections, consider using protocols such as Secure Ethernet (MACsec).
- Secure Configurations: Network devices should be securely configured to avoid unauthorized access or manipulation. This involves password protection, regular firmware updates, and disabling unnecessary services and features.
- Network Access Control (NAC): NAC systems can be used to limit the capabilities of and access to the network for unrecognized devices.
- Internet Layer: The internet layer is responsible for IP addressing and routing, carrying packets from the source host to the destination host across multiple networks.
- Internet Protocol Security (IPSec): IPSec can be used to secure communications over IP networks through the use of cryptographic security services.
- Ingress and Egress Filtering: Use ingress filtering to prevent IP spoofing (i.e., when a malicious party sends IP packets with a false source address). Egress filtering can stop your network from being used in denial-of-service attacks.
- Routing Protocol Security: Use secure routing protocols (like BGPsec for BGP) or add security to existing protocols to prevent attacks on the routing infrastructure.
- Transport Layer: This layer is responsible for end-to-end communication services for applications. It provides mechanisms for the reliable transmission of data.
- Transport Layer Security (TLS): TLS can secure connections by providing encryption, data integrity, and authentication. Use the latest TLS version to protect against known vulnerabilities in earlier versions.
- Secure Sockets Layer (SSL): Though deprecated, SSL is still widely used. If you must use SSL, use the latest version and patch vulnerabilities.
- Stateful Firewalls: These can monitor the state of active connections and use this information to permit or deny new connection requests.
- Application Layer: This topmost layer of the TCP/IP model provides services for end-user applications. Security at this layer is critical as it's the closest to the user.
- Secure Application Design: Incorporate security principles in application development processes, such as secure coding practices, code reviews, and regular updates and patches.
- Authentication and Authorization: Implement strong user authentication mechanisms, like two-factor or multi-factor authentication. Maintain strict authorization practices to ensure users can only access data and services for which they have permissions.
- Content Filtering and Web Application Firewalls (WAFs): Filter out malicious content and use WAFs to protect your web applications from common exploits and vulnerabilities.
- Cross-layer considerations: While each layer presents its unique challenges, it's vital to consider strategies that cut across the entire TCP/IP stack.
- Security Policies and Procedures: Develop a comprehensive set of policies and procedures that cover all aspects of network security. These should be regularly reviewed and updated as necessary.
- Monitoring and Logging: Implement robust monitoring solutions to detect anomalies and intrusions. Combine this with comprehensive logging to provide an audit trail for forensic analysis and ongoing security improvement.
- Incident Response: Develop a clear incident response plan. This should detail the steps to be taken in the event of a security incident, from initial identification and containment,
- Incident Response: Develop a clear incident response plan. This should detail the steps to be taken in the event of a security incident, from initial identification and containment, through to remediation and recovery, and finally, post-incident analysis to learn from the event.
- Security Training: Invest in regular security training and awareness programs for all users of your network. Many security breaches occur due to human error or ignorance, making this an essential preventative measure.
- Regular Audits and Assessments: Conduct frequent security audits and risk assessments to uncover vulnerabilities and assess the effectiveness of your security controls. Use tools like vulnerability scanners and penetration testing to discover potential weaknesses.
- Zero Trust Architecture: Implement a zero trust approach to security. In a zero trust model, all users and devices, whether inside or outside the network, are treated as untrusted. This means verifying and validating all access attempts, typically through multi-factor authentication, least-privilege access, and ongoing monitoring.
- Security by Design: Make security an integral part of your network architecture and application design, rather than an afterthought. This should include implementing principles such as least privilege, separation of duties, and defense in depth.
To summarize, securing the TCP/IP protocol stack is a complex task, requiring a multi-layered approach that addresses the unique challenges and vulnerabilities of each layer. It is not enough to focus on one layer at the expense of others; a single weak point can lead to a full-scale security breach. Therefore, security must be a comprehensive, end-to-end effort that considers the stack as a whole, supplemented by robust policies, procedures, and ongoing vigilance. Remember, in cybersecurity, prevention is always better than cure.
[1]Packet sniffing: the activity in which a hacker can intercept and read datagram packets, is common.
[2](VPN) Virtual Private Network: An extended local area network (LAN) that enables an organization to conduct secure, real-time communication.