Security Standards and Services
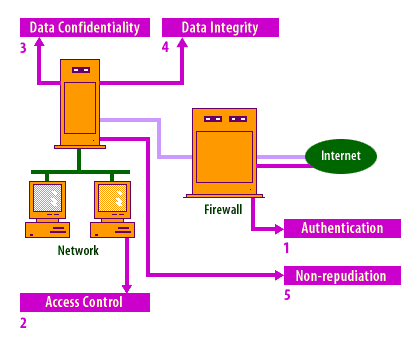
Authentication
The process of proving identity, authentication services ensure the authenticity of an entity during communication and/or transfer of data.
Access control
Access control provides protection against the unauthorized use of system resources that may be accessible. This service
relates to what resources a user or service may access on the system or network.
Question:
What roles do 1) data confidentiality, 2) data integrity and 3) non-repudiation have within the context of Security Standards?
Data confidentiality
Data confidentiality services protect data from unauthorized disclosure and passive threats.
Data confidentiality is a key aspect of security standards that ensures sensitive information is protected from unauthorized access, disclosure, or tampering. This can be achieved through various techniques such as encryption, access control mechanisms, and secure authentication methods. Maintaining data confidentiality is essential for protecting an organization's intellectual property, trade secrets, customer data, and other sensitive information that, if disclosed to unauthorized parties, could result in significant damage to the organization's reputation, financial standing, or competitive advantage. Compliance with security standards, such as the GDPR or the Health Insurance Portability and Accountability Act (HIPAA), requires organizations to implement strict measures to ensure data confidentiality.
Data confidentiality is a key aspect of security standards that ensures sensitive information is protected from unauthorized access, disclosure, or tampering. This can be achieved through various techniques such as encryption, access control mechanisms, and secure authentication methods. Maintaining data confidentiality is essential for protecting an organization's intellectual property, trade secrets, customer data, and other sensitive information that, if disclosed to unauthorized parties, could result in significant damage to the organization's reputation, financial standing, or competitive advantage. Compliance with security standards, such as the GDPR or the Health Insurance Portability and Accountability Act (HIPAA), requires organizations to implement strict measures to ensure data confidentiality.
Data integrity
Data integrity services protect against active threats by verifying or maintaining the consistency of information.
Data integrity refers to the accuracy, consistency, and reliability of data over its entire lifecycle. Security standards emphasize the importance of maintaining data integrity to ensure that information remains unaltered and uncompromised from creation to storage, transmission, and eventual disposal. Data integrity is critical for the correct functioning of applications, systems, and decision-making processes within an organization. Techniques used to maintain data integrity include checksums, hashing, digital signatures, and version control. Various security standards, such as ISO/IEC 27001 and the Payment Card Industry Data Security Standard (PCI DSS), require organizations to implement measures that ensure data integrity.
Data integrity refers to the accuracy, consistency, and reliability of data over its entire lifecycle. Security standards emphasize the importance of maintaining data integrity to ensure that information remains unaltered and uncompromised from creation to storage, transmission, and eventual disposal. Data integrity is critical for the correct functioning of applications, systems, and decision-making processes within an organization. Techniques used to maintain data integrity include checksums, hashing, digital signatures, and version control. Various security standards, such as ISO/IEC 27001 and the Payment Card Industry Data Security Standard (PCI DSS), require organizations to implement measures that ensure data integrity.
Non-repudiation
Repudiation is defined as the denial by one of the entities involved in a communication of having participated in all or part of the communication. Non-repudiation services provide for proof of origin and/or proof of delivery.
Non-repudiation is an essential element of security standards that ensures the authenticity of a communication, transaction, or digital document by providing irrefutable proof of its origin, receipt, and possible modification. This prevents parties involved in a transaction or communication from denying their participation or the validity of the exchanged information. Non-repudiation plays a crucial role in ensuring trust and accountability in digital interactions, particularly in e-commerce, financial transactions, and legal documents. Techniques used to establish non-repudiation include digital signatures, timestamps, and public key infrastructure (PKI). Security standards, such as the Electronic Signatures in Global and National Commerce Act (ESIGN) and the European Union's eIDAS regulation, provide guidelines for implementing non-repudiation mechanisms to ensure secure and legally binding digital transactions.
Non-repudiation is an essential element of security standards that ensures the authenticity of a communication, transaction, or digital document by providing irrefutable proof of its origin, receipt, and possible modification. This prevents parties involved in a transaction or communication from denying their participation or the validity of the exchanged information. Non-repudiation plays a crucial role in ensuring trust and accountability in digital interactions, particularly in e-commerce, financial transactions, and legal documents. Techniques used to establish non-repudiation include digital signatures, timestamps, and public key infrastructure (PKI). Security standards, such as the Electronic Signatures in Global and National Commerce Act (ESIGN) and the European Union's eIDAS regulation, provide guidelines for implementing non-repudiation mechanisms to ensure secure and legally binding digital transactions.