| Lesson 3 | Understanding Security System Threats |
| Objective | Identify and describe the main types of system threats that compromise network security. |
System Threats in Network Security
In network security, a threat refers to any event or actor that can exploit a vulnerability to cause harm, disrupt operations, or gain unauthorized access. Understanding the major categories of system threats is the first step in developing effective countermeasures.
1. Malware and Software-Based Threats
Malware encompasses any program intentionally designed to cause damage or unauthorized actions on a system. Common types include:
- Viruses: Malicious code that attaches to legitimate files and spreads when the infected file is executed.
- Worms: Self-replicating programs that spread through networks without user interaction.
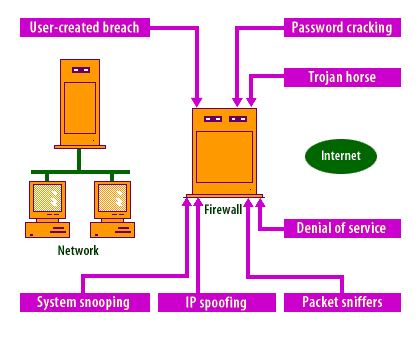
- Trojans: Legitimate-looking software that conceals harmful code to steal or destroy data.
- Ransomware: Encrypts data and demands payment for its release.
- Spyware: Secretly monitors user activity, capturing keystrokes and personal information.
2. Password Attacks and Brute-Force Methods
Attackers frequently attempt to obtain user credentials using various password-cracking methods. Dictionary attacks test lists of common passwords, while brute-force attacks try all possible combinations of characters until a match is found. Strong passwords containing uppercase, lowercase, numeric, and special characters make such attacks exponentially harder.
3. Network Exploits
Network-based threats exploit weaknesses in communication protocols or services:
- Denial of Service (DoS/DDoS): Overwhelming a network or server with traffic to make it unavailable to legitimate users.
- Packet Sniffing: Monitoring network traffic to intercept sensitive data.
- IP Spoofing: Forging source IP addresses to impersonate trusted systems.
- Man-in-the-Middle (MitM): Intercepting communications to steal or alter information.
4. Coding and Software Vulnerabilities
Unpatched software and poor coding practices can create entry points for attackers:
- Buffer Overflow: Overwriting memory by sending more data than a program expects, allowing code injection.
- Back Doors: Intentional or accidental access points left in software for maintenance or testing that can be exploited.
- Configuration Errors: Misconfigured servers or devices that leave data or services exposed to unauthorized access.
5. Social Engineering
Social engineering manipulates human psychology rather than technical vulnerabilities. Attackers may impersonate legitimate users, IT staff, or vendors to extract credentials or sensitive information.
- Phishing: Fraudulent emails or websites designed to trick users into sharing credentials or installing malware.
- Pretexting: Fabricating scenarios or identities to deceive victims into revealing confidential information.
- Baiting: Using physical or digital lures (e.g., infected USB drives) to compromise systems.
6. Internal and Insider Threats
Not all threats originate outside the organization. Insiders—employees, contractors, or vendors—may intentionally or accidentally compromise security.
- Malicious Insiders: Individuals abusing their legitimate access for theft or sabotage.
- Accidental Actions: Users inadvertently causing breaches by mishandling sensitive data or ignoring policies.
7. Physical and Environmental Threats
Security breaches are not always digital. Physical security remains a core component of network protection:
- Unauthorized Access: Physical intrusions into data centers or theft of devices.
- Environmental Events: Fires, floods, or power failures that can damage hardware or cause downtime.
8. Potential Threats to Organizational Resources
System threats can target multiple resource domains within an organization:
- Local Resources: Malware or malicious applets damaging end-user devices.
- Network Resources: IP spoofing, system snooping, and data interception.
- Server Resources: Unauthorized access, service interruption, or trojan installations.
- Database Resources: Theft of intellectual property, customer data, or trade secrets.
Key Takeaways
- Every system contains vulnerabilities that can be exploited by a corresponding threat.
- Comprehensive security requires a combination of technology, process, and user awareness.
- Legacy algorithms like DES should be replaced with AES for encryption and SHA-256+ for hashing.
- Use service accounts with least privilege and rotate credentials regularly.
By recognizing these threat categories, administrators can proactively implement safeguards—patching software, hardening configurations, training users, and monitoring network activity—to reduce the likelihood and impact of attacks.