| Lesson 5 | Transport layer (TCP/UDP) |
| Objective | Identify the Transport Layer (TCP/UDP) and its weaknesses |
Identify Transport Layerand its weaknesses
The transport layer controls the flow of information between hosts. Two protocols exist at the transport layer, the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP). These two protocols use ports for directing information, which are key to implementing Internet security measures.
- TCP/IP Transport Layer:
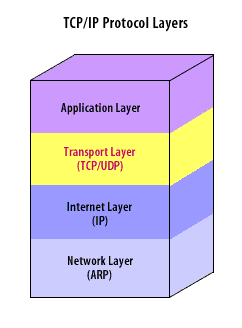
- Application Layer
- (TCP/UDP) Transport Layer
- (IP) Internet Layer
- (ARP) Network Layer
Transmission Control Protocol (TCP)
TCP is a connection-oriented protocol using a "handshaking" process and an information exchange to complete a connection upon which traffic passes. TCP is the protocol used by most Internet services, including HTTP (the World Wide Web), FTP, and SMTP (email).
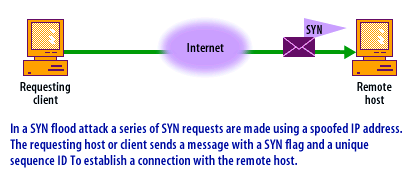
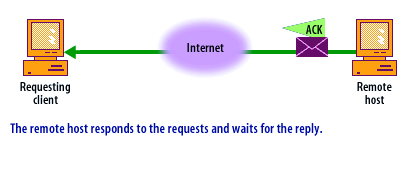
- TCP handshake: The TCP handshake is a common area of attack. What happens in the TCP handshake process when a connection is established and when it is attacked is shown in the following series of images.
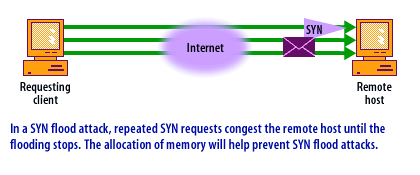
SYN Flood Attack - Transport Layer
A SYN Flood attack is a form of Denial-of-Service (DoS) attack that exploits the three-way handshake mechanism of the Transmission Control Protocol (TCP), a core protocol in the Transport Layer of the TCP/IP suite. This mechanism is essential for establishing connections between two hosts in a TCP network.
The three-way handshake process includes the following steps:
A SYN Flood attack abuses this process with the aim of exhausting a target system's resources and rendering it unresponsive to legitimate traffic. The attack's specific characteristics are:
In the face of such threats, network administrators should deploy strategies to detect and mitigate SYN Flood attacks. These can include setting sensible SYN Received timeouts, implementing SYN cookies, deploying intrusion detection and prevention systems (IDS/IPS), or configuring firewalls to limit the rate of SYN packets from a single source.
- The initiating host (Client) sends a SYN (synchronization) packet to the host it wishes to connect to (Server). This packet signals the client's intent to establish a communication channel.
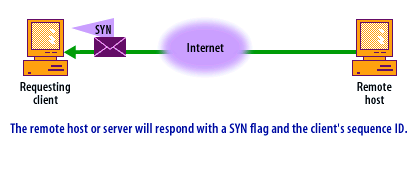
- The receiving host (Server) acknowledges the request by sending a SYN-ACK (synchronization-acknowledged) packet back to the client.
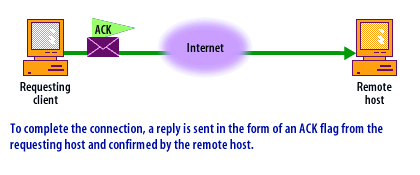
- The initiating host (Client) then acknowledges the server's SYN-ACK with an ACK (acknowledgment) packet. After this step, the connection is established and data transfer can begin.
A SYN Flood attack abuses this process with the aim of exhausting a target system's resources and rendering it unresponsive to legitimate traffic. The attack's specific characteristics are:
- High Volume of SYN Packets: The attacker sends a rapid succession of SYN packets to the target host, often using a botnet or other means to generate a massive amount of traffic. This overwhelms the target's ability to process incoming connection requests.
- Spoofed Source IP Addresses: The SYN packets typically have a falsified source IP address. This makes it difficult for the victim to respond to the SYN-ACK packet, as it is sent to an IP address that didn't originate the request. This also makes it harder to trace the attack back to the actual source.
- Incomplete Handshakes: As the attacker does not respond to the SYN-ACK packets sent by the victim, a significant number of half-open connections are left on the victim's system. These connections are in a state known as "SYN_RECEIVED."
- Resource Exhaustion: Each half-open connection consumes resources on the victim's system. When the number of such connections crosses a certain threshold, the system can no longer accept new connection requests. Legitimate users trying to connect to the system are then denied service.
In the face of such threats, network administrators should deploy strategies to detect and mitigate SYN Flood attacks. These can include setting sensible SYN Received timeouts, implementing SYN cookies, deploying intrusion detection and prevention systems (IDS/IPS), or configuring firewalls to limit the rate of SYN packets from a single source.
User Datagram Protocol (UDP)
UDP is a connectionless protocol often used for broadcast-type protocols, such as audio or video traffic.
Because a host issues a UDP message and does not expect a reply, embedding malicious activities within these types of datagrams is difficult. In addition, it is possible to flood a port with UDP attacks.
- TCP or UDP Port: A machine running TCP/IP almost always has many different applications running at the same time, and all must be able to communicate simultaneously. Security is largely contingent upon the proper directing of network packets. Each application is assigned a specific TCP or UDP port number and incoming network packets are directed to the correct application by the operating system. There are 65,536 possible ports that can be used with either TCP or UDP. The Internet Assigned Numbers Authority (IANA) assigns and maintains port numbers including well-known ports, registered ports, and private ports. IANA has defined the first 1023 ports as reserved for specific server-side applications. Some examples are shown in the table below.
TCP/IP Protocol Suite
Internet Assigned Numbers Authority (IANA):
Oversees and coordinates the assignment of every unique protocol identifier used on the Internet.
To configure firewalls for use with DNS, you need to understand how UDP works.
| Program / Application | Standard Port |
| (FTP) File transfer protocol | TCP 20 and TCP 21 |
| (DNS) Domain name server | TCP 53 and UDP 53 |
| (HTTP) Web Server | TCP 80 |
| (SNMP) Simple Network Management Protocol | UDP 161 and UDP 162 |
| (SMTP) Mail servers Using Simple Mail Transfer Protocol | TCP 25 |
| (NNTP) Network News Transfer Protocol | TCP 119 |
| Telnet | TCP port 23 |
To configure firewalls for use with DNS, you need to understand how UDP works.