| Lesson 2 | TCP/IP and network security |
| Objective | Network security is affected at TCP/IP levels. |
TCP/IP and Network Security
Objective: Understand how security is implemented—and attacked—across the TCP/IP layers, and how to choose controls that harden each layer.
The Internet’s original protocols prioritized interoperability and reliability over security. Today, attackers routinely probe the TCP/IP stack, abusing weak configurations and legacy services. Defenders must understand how packets are built and routed, where trust boundaries exist, and which controls reduce risk at each layer. Modern baselines favor TLS (successor to SSL), AES for confidentiality, and SHA-256+ for integrity, replacing legacy mechanisms such as DES.
The TCP/IP Stack at a Glance
Before diving into defenses, review the functional layers and their typical responsibilities. The first figure summarizes the four TCP/IP layers.
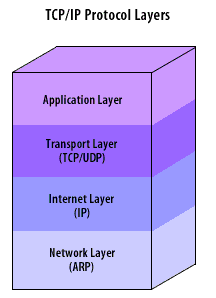
- Application Layer: In the application layer, a client-side application is used to initiate communication with other hosts.
- Transport layer (TCP/UDP): The transport layer uses two protocols, TCP and UDP, to control the flow of information between hosts. TCP is responsible for placing a message into datagrams, reassembling the datagrams upon arrival at their destination, and resending anything that gets lost.
- Internet layer (IP): The Internet protocol (IP) layer is used primarily for addressing hosts and routing, and does not provide any means for error correction or flow control.
- Network layer: Signals are transmitted across the network layer.
How Security Is Affected at Each TCP/IP Layer
- Link/Network Access (on LAN/WAN edges): Risks include MAC spoofing, ARP poisoning, rogue APs, and physical tampering. Controls: 802.1X port-based access control, NAC policies, DHCP snooping & IP/MAC binding, dynamic ARP inspection, VLAN segmentation, wireless WPA3-Enterprise, and MACsec for link encryption.
- Internet (IP) Layer: Risks include IP spoofing, route hijacking, and fragmentation abuse. Controls: Ingress/egress filtering (BCP 38/84), strict antispoof ACLs on borders, IPsec for authenticated/encrypted tunnels, and hardened routing (uRPF where appropriate).
- Transport Layer (TCP/UDP): Threats include SYN floods, reset injection, reflection/amplification via UDP services, and blind spoofing. Controls: Stateful firewalls, SYN cookies, rate limiting, selective ACK tuning, disabling/discouraging insecure UDP services, and strict allowlists. Observe ports with NetFlow/IPFIX.
- Application Layer: Most breaches occur here (HTTP(S), DNS, SMTP, APIs). Controls: TLS with modern ciphers, strong authentication and MFA, least-privilege authorization, input validation, WAFs/WAAP for L7 filtering, secure headers (HSTS, CSP), and service isolation via mTLS and service meshes where applicable.
Mapping to OSI for Conceptual Clarity
Although real networks speak TCP/IP, the OSI model remains a useful reference for teaching responsibilities and comparing controls. The second figure shows a conceptual correlation between OSI layers and TCP/IP.
Network Security and Firewalls
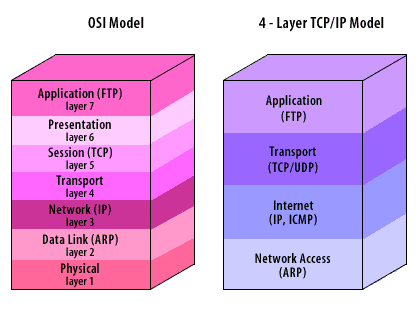
| Layer | Classification | Protocol |
|---|---|---|
| 1 | Physcial | |
| 2 | Data Link | (ARP) =Address Resolution Protocol |
| 3 | Network | (IP) = Internet Protocol |
| 4 | Transport | |
| 5 | Session | (TCP)= Transfer Control Protocol |
| 6 | Presentation | |
| 7 | Application | (FTP) = File Transport Protocol |
- Physcial = Layer 1
- (ARP) Data Link = Layer 2
- (IP) Network = Layer 3
- Transport = Layer 4
- (TCP) Session = Layer 5
- Presentation = Layer 6
- (FTP) Application = Layer 7
The TPC/IP Model contains 4 layers.
- (FTP) Application
- (TCP/UDP) Transport
- (IP, ICMP) Internet
- (ARP) Network Access
Designing Firewall Policies for TCP/IP
Effective firewalling starts with architecture, not rules:
- Segment first: Split environments (prod/test/dev), tier apps (web, app, DB), and isolate management planes.
- Default-deny posture: Allow only required flows, from trusted sources, to known destinations, on justified ports.
- Validate with packet capture: Use
tcpdumporWiresharkto confirm intended behavior and detect leaks. - Log and review: Centralize logs, baseline normal traffic, and alert on anomalies (e.g., unexpected egress DNS/SMTP).
- Modern crypto: Prefer TLS 1.2/1.3 with AEAD ciphers; deprecate DES/RC4/MD5; use SHA-256+ for integrity (per site policy).
Interoperability Notes
Applications choose TCP for reliability (ordering, retransmission) or UDP for low-latency datagrams. Both encapsulate into IP, which relies on ARP (on local segments) to resolve MAC addresses. Healthy interoperability requires consistent MTU settings, ECN awareness, and careful load-balancer/NAT behavior (session affinity where needed). Document these expectations so firewall rules, NAT, and observability remain aligned.
Quick Reference
- Common weak points: open administrative ports, unauthenticated UDP services, permissive egress, legacy clear-text protocols.
- High-value controls: MFA everywhere possible, strict egress control, L7 validation, IPsec/mTLS for service-to-service trust, and key rotation.
- Operational cadence: quarterly rule recertification, monthly vulnerability remediation, continuous monitoring.
Terminology
IP: Logical addressing and routing for hosts on an internetwork.
ICMP: Signaling at the IP layer (e.g., errors, diagnostics).
TCP/IP: The suite that encapsulates application data into packets routed across networks.
UDP: Connectionless transport used for latency-sensitive or broadcast/multicast scenarios.
OSI: A seven-layer conceptual model used to describe and reason about network communication.