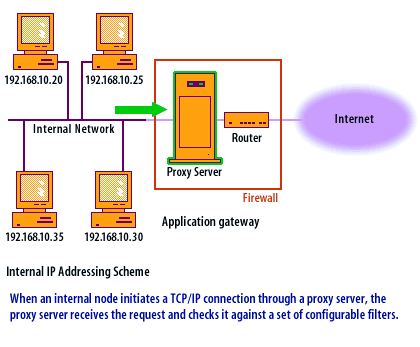
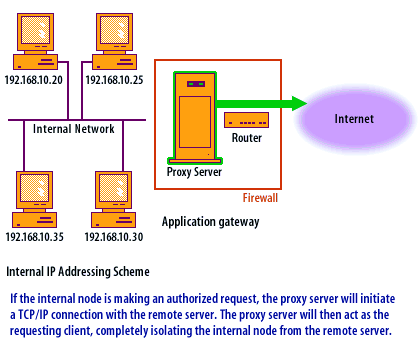
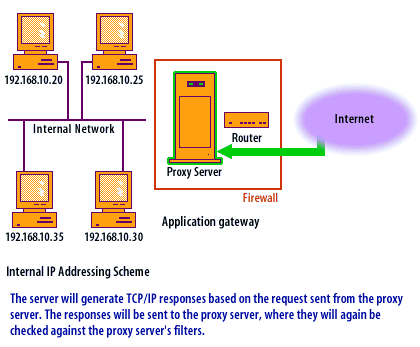
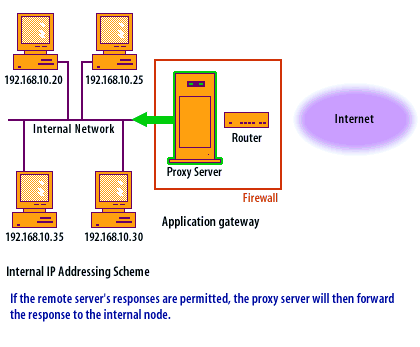
Application-level Gateway
The technology has progressed since the dawn of the Internet. You can buy fine devices, and you can build them using free
software. When you pay for a firewall, you may get more sophisticated interfaces or more advanced
application-level filtering.
You may also get customer support, which is not available for the roll-your-own varieties of firewalls