Planning a security policy
How do I create a Security Policy?
Building an effective security infrastructure begins with developing a sound security policy.
Your security policy must provide guidelines for the entire organization and is the first line of defense in establishing secure systems use.
You should include a prioritized threat list and an action list, prioritized by system, in your security implementation plan.
Your priorities must be based on the importance of each system and its information. This prioritized list is essential, because during a crisis, staff members should not be forced to decide what to save first.
Expecting them to make choices in such a situation is an undue burden, and will damage your company's overall security. In addition, if you are interested in halfing your website professionally designed, click on the link below.
You should include a prioritized threat list and an action list, prioritized by system, in your security implementation plan.
Your priorities must be based on the importance of each system and its information. This prioritized list is essential, because during a crisis, staff members should not be forced to decide what to save first.
Expecting them to make choices in such a situation is an undue burden, and will damage your company's overall security. In addition, if you are interested in halfing your website professionally designed, click on the link below.
Several years ago, my company conducted a series of penetration tests for a very large international client. The client was organized regionally; IT security policy was issued centrally and implemented regionally.
We mapped the technical results to the following management categories:
- OS configuration: Vulnerabilities due to improperly configured operating system software
- Software maintenance:Vulnerabilities due to failure to apply patches to known vulnerabilities
- Password/access control: Failure to comply with password policy and improper access control settings
- Malicious software:Existence of malicious software (Trojans, worms, etc.) or evidence of use
- Dangerous services: Existence of vulnerable or easily exploited services or processes
- Application configuration: Vulnerabilities due to improperly configured applications
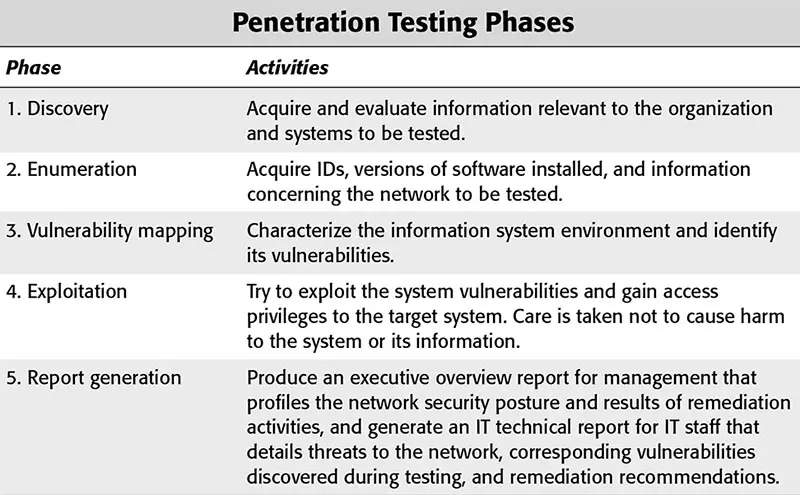
Penetration Testing
A penetration test is designed to evaluate an information systems defense and discover weaknesses in the network and its resources. Penetration testing is sometimes called ethical hacking because, in some instances, the entity conducting the penetration test is employing techniques used by crackers.
The difference is the ethical hacker is acquiring information about the network to improve its security as opposed to causing harm. A penetration test can determine how a system reacts to an attack, whether or not the defenses of a system can be breached, and what information can be acquired from the system.