| Lesson 2 | Understanding procmail |
| Objective | Describe procmail and its use. |
Understanding procmail
The Linux email system is very straightforward: mail from an external site is
routed to a local network's mail handler, where users retrieve the mail using their favorite email program. This system doesn't offer any
intrinsic, automatic filtering or manipulation functionality.
procmail was developed to fill this need. With procmail, administrators and users can automatically filter and manipulate their incoming email in a variety of ways. It is designed to:
- filter the mail based on the email's header or body content
- save the email into a mail folder other than the default
- send the email to another program for processing
- throw the email into the trash can
procmail takes over after the local mail handler receives an email. The FlipBook below illustrates this process.
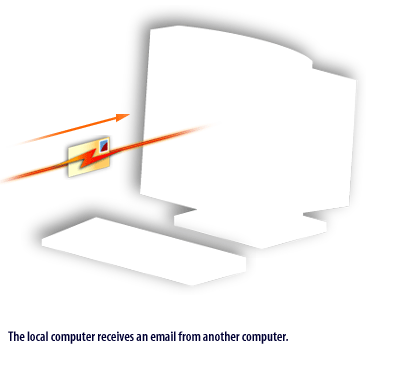
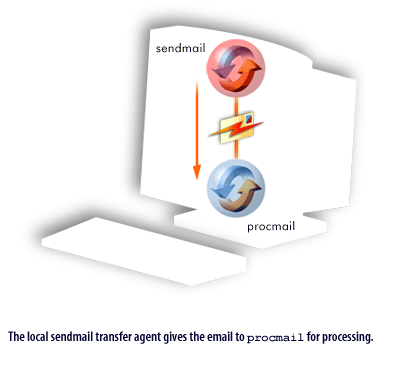
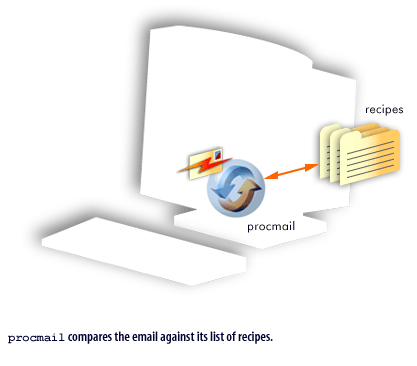
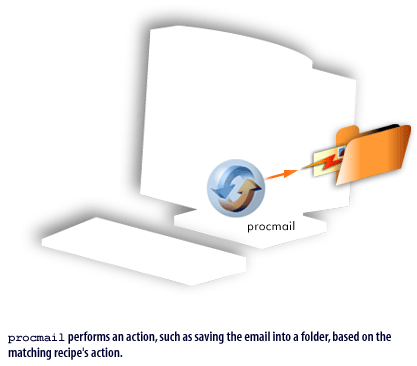
Preventing SPAM with procmail
procmail is often used as a weapon against SPAM. Because procmail inspects every email that passes through and filters the email based on your recipes, it is perfectly suited to eliminating unwanted email.There are two popular
procmail SPAM filters:
Spam Bouncer and junkfilter. Both filters offer the same basic functionality, but their specific installation and configuration details differ significantly.
junkfilter is easy to install and configure, and it is best suited for users who don't want to spend much time configuring their email filters. Spam Bouncer is more difficult to install, but it is more robust and offers a wide range of advanced functionality.
Tools to prevent email spam
Question: In Red Hat Linux, which type of tools exist to prevent email spam?
Red Hat Linux provides several tools that can be used to prevent email spam and improve email security.
Some of the most commonly used tools are:
By using a combination of these tools and techniques, Red Hat Linux administrators can significantly reduce the amount of spam and other unwanted email that reaches users' inboxes, improving email security and reducing the risk of email-based attacks.
- SpamAssassin: SpamAssassin is an open-source, anti-spam software that uses a range of techniques to identify and filter out spam emails. It can be integrated with most email clients and servers, and provides a customizable set of rules and filters to identify and block spam messages.
- Postgrey: Postgrey is a greylisting tool that can be used to block spam emails by temporarily rejecting emails from unknown senders. When an email is received, Postgrey checks the sender's IP address against a whitelist of known, trusted senders. If the sender is not on the whitelist, the email is temporarily rejected. Most spam emails are sent from compromised machines or bots, which will not retry the delivery, thus effectively blocking the spam.
- ClamAV: ClamAV is an open-source antivirus software that can be used to scan incoming emails for malware and viruses. It can be integrated with most email clients and servers, and provides a customizable set of rules and filters to detect and block malicious attachments and links.
- DNSBLs (DNS Blacklists): DNSBLs are lists of IP addresses and domains that have been identified as sources of spam or other malicious activity. Email servers can be configured to use DNSBLs to reject or flag emails from these sources, thereby reducing the amount of spam that reaches users' inboxes. [1]
- SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail): These are email authentication protocols that can be used to verify the authenticity of incoming emails. SPF allows domain owners to specify which IP addresses are authorized to send emails on behalf of their domains, while DKIM uses digital signatures to verify that emails have not been tampered with in transit.
By using a combination of these tools and techniques, Red Hat Linux administrators can significantly reduce the amount of spam and other unwanted email that reaches users' inboxes, improving email security and reducing the risk of email-based attacks.
In the next lesson, you'll learn to configure
procmail.
[1]Inbox: A user's primary email mailbox, into which all unfiltered mail flows.