| Lesson 7 | Insecure remote login |
| Objective | Describe Insecure Remote Login Services |
Insecure Remote Login using Redhat Linux
Remote login is provided by a number of network services.
These services allow users to connect and use a machine from across the network.
However, many of these services give crackers an easy way to access your machine, by either sending everything in clear text or by allowing anonymous logins.
The information below describes various vulnerabilities opened by remote login services, password-free logins, and allowing other machines to access your system.
The information below describes various vulnerabilities opened by remote login services, password-free logins, and allowing other machines to access your system.
Common remote login Services
Telnet is the most common remote login service. Your password and everything you send, including other passwords,
is transmitted in clear text across the network.
Linux utilities and functions, such as
To create a secure environment, disable these utilities.
rlogin, rsh, and rexec allow users to easily login and execute commands on remote machines. However, everything is transmitted without encryption.To create a secure environment, disable these utilities.
Disable password-free Logins
You should never provide public, password-free accounts on your machine. If you must provide public access, use a face-to-face password transfer and change your passwords often. To disable password-free login, edit the files
/etc/pam.d/rlogin and
/etc/pam.d/rshand reconfigure the security settings contained in these files.
View the series of images below to review how to disable password-free logins.
Disabling password-free logins
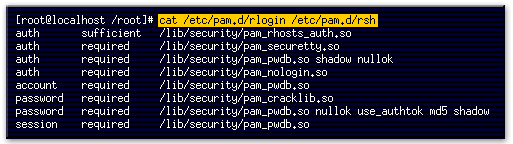
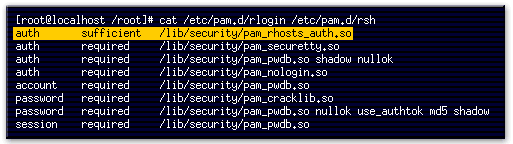
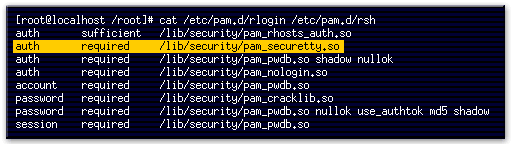
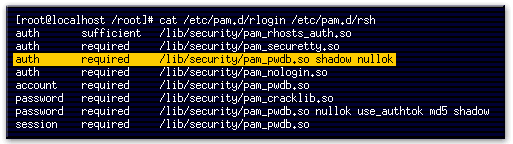
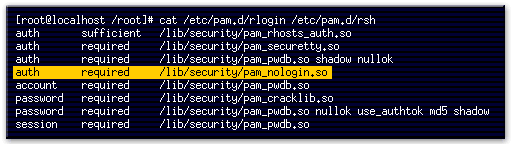
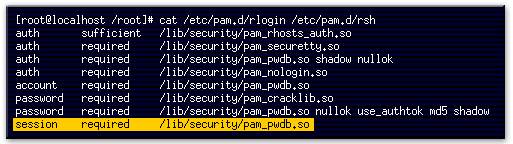
- This command displays the contents of the rlogin and rsh PAM authorization files.
- This line indicates that users can use a .rhosts file in their home directory to allow password-free logins.
- This line indicates that if the user is trying to log in as root, the tty on which they are logging
- This line will cause the system to ask the user for a password and will check the password.
- This line checks to see if the file /etc/nologin exists.
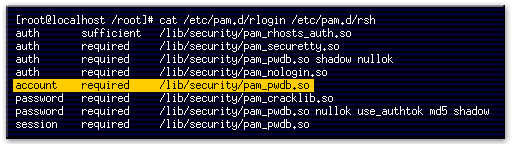
- This line instructs the system to compare the user's attributes (stored in the password database) against system limits.
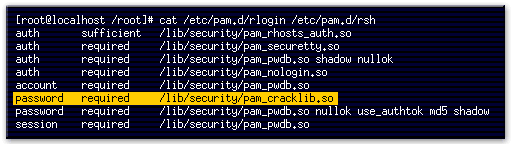
- This line subjects a newly changed password to a series of tests to ensure that it cannot be easily determined by a dictionary-based password cracking program.
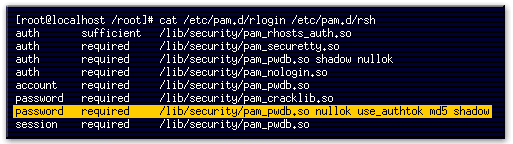
- This line specifies that if the login program changes the user's password, it should use the pam_pwdb.so module to do so.
- This line specifies that the pam_pwdb.so module should be used to manage the session.
Commands to disable password-free Logins in Red Hat Linux
To disable password-free logins in Red Hat Linux, you can follow these steps:
With these steps, you have disabled password-free logins in Red Hat Linux. This will require users to provide a password or other authentication method to log in to the system. It is generally recommended to use some form of authentication to secure access to your Linux system.
- Open a terminal window on your Red Hat Linux system.
- Edit the sshd configuration file using the following command:
sudo vi /etc/ssh/sshd_config
- Locate the line that reads "PermitEmptyPasswords yes" and change it to "PermitEmptyPasswords no".
- Save the changes to the configuration file and exit the text editor.
- Restart the sshd service using the following command:
sudo systemctl restart sshd
With these steps, you have disabled password-free logins in Red Hat Linux. This will require users to provide a password or other authentication method to log in to the system. It is generally recommended to use some form of authentication to secure access to your Linux system.
.rhosts and /etc/hosts. equiv
The
Question: What command is inserted into the /etc/pam.d/rlogin file to disable password-free logins?
Answer:
The next lesson discusses secure remote login services.
/etc/hosts.equiv file lists "administratively equivalent" hosts, from which users can connect without a password; for example, bob on machine1 can
connect as bob on machine2 without a password, if machine1 is listed in machine2''s /etc/hosts.equiv file.
The .rhosts file in anyone's home directory lists the users and the machines that can connect as that user without using a password. The authentication service used to determine whether to allow a connection is totally insecure. Even if connections are restricted to just the local network, a compromise of one machine on your network can
instantly lead to a compromise of your entire network.
Question: What command is inserted into the /etc/pam.d/rlogin file to disable password-free logins?
Answer:
[redhat@localhost redhat]$auth required /lib/security/pam_nologin.so
Red Hat Reference