| Lesson 8 | Secure remote login |
| Objective | Describe secure remote login services. |
Secure remote login using Redhat Linux
In this day and age, the provision of unencrypted remote login is an unnecessary and gaping security hole.
There are now tools available that provide secure, encrypted, and authenticated remote login and command execution facilities. Use tools such as
There are now tools available that provide secure, encrypted, and authenticated remote login and command execution facilities. Use tools such as
ssh (a secure, encrypted shell) instead of insecure remote login services like telnet.
Scrap the insecure and use ssh
The
You should install these tools and then disable all your other remote login methods, except, perhaps, for one service usable only by administrators from the local network in an emergency. Also, since crackers are constantly finding ways to break in, you should always use the latest version of
Since
The following series of images walks you through an example of a secure access process.
OpenSSH tool provides secure, encrypted, and authenticated remote login and command execution facilities.
The OpenSSH utility is available for download from many sites.You should install these tools and then disable all your other remote login methods, except, perhaps, for one service usable only by administrators from the local network in an emergency. Also, since crackers are constantly finding ways to break in, you should always use the latest version of
OpenSSH.
Since
ftp is also a large security hole, you should use scp
Secure Copy, a remote file copy program) instead. scp uses ssh authentication and encryption for copying files across hosts. The following series of images walks you through an example of a secure access process.
Secure Access Process
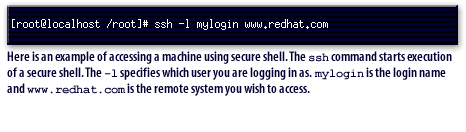
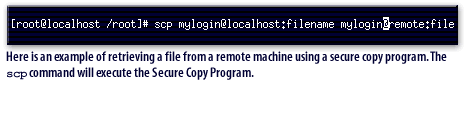
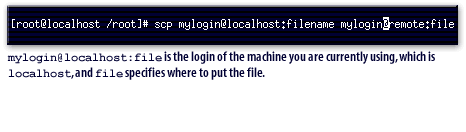
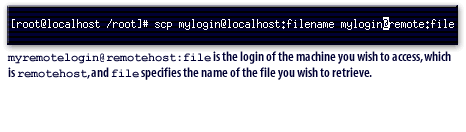
Secure Remote Login Access
Why Use SSH?
Potential intruders have a variety of tools at their disposal enabling them to disrupt, intercept, and reroute network traffic in an effort to gain access to a system. In general terms, these threats can be categorized as follows:
Interception of communication between two systems
The attacker can be somewhere on the network between the communicating parties, copying any information passed between them. He may intercept and keep the information, or alter the information and send it on to the intended recipient. This attack is usually performed using a packet sniffer, a rather common network utility that captures each packet flowing through the network, and analyzes its content.
Impersonation of a particular host
Attacker's system is configured to pose as the intended recipient of a transmission. If this strategy works, the user's system remains unaware that it is communicating with the wrong host. This attack can be performed using a technique known as DNS poisoning, or via so-called IP
spoofing. In the first case, the intruder uses a cracked D NS server to point client systems to a maliciously duplicated host. In the second case, the intruder sends falsified network packets that appear to be from a trusted host.
Both techniques intercept potentially sensitive information and, if the interception is made for hostile reasons, the results can be disastrous. If SSH is used for remote shell login and file copying, these security threats can be greatly diminished. This is because the SSH client and server use digital signatures to verify their identity. Additionally, all communication between the client and server systems is encrypted. Attempts to spoof the identity of either side of a communication does not work, since each packet is encrypted using a key known only by the local and remote systems.
Both techniques intercept potentially sensitive information and, if the interception is made for hostile reasons, the results can be disastrous. If SSH is used for remote shell login and file copying, these security threats can be greatly diminished. This is because the SSH client and server use digital signatures to verify their identity. Additionally, all communication between the client and server systems is encrypted. Attempts to spoof the identity of either side of a communication does not work, since each packet is encrypted using a key known only by the local and remote systems.
The next lesson explains how to control root login access.
Click on the link below to learn more about the Secure Shell and Secure Copy Program.
Secure Shell and Secure Copy Program
Secure Shell and Secure Copy Program
Red Hat Reference