| Lesson 4 | Process auditing |
| Objective | Describe process auditing. |
Process Auditing in Red Hat Linux
Question: Does process auditing involve examining the process accounting logs and retrieving useful information in Red Hat Linux?
Yes, process auditing in Red Hat Linux indeed involves the examination of process accounting logs to extract useful information. However, it's essential to understand that process auditing and process accounting, while interconnected, are distinct concepts. Process accounting is the mechanism that tracks system usage statistics and activities of each process and command executed in the system. This includes details like CPU usage, memory consumption, command execution times, and the users who initiated these commands. On the other hand, process auditing refers to the systematic review and analysis of these process accounting logs. The primary aims of process auditing are:
In summary, process auditing in Red Hat Linux involves a thorough analysis of the process accounting logs to retrieve crucial information. This practice enhances system security, optimizes performance, enables efficient troubleshooting, ensures user accountability, and assists in forensic analysis, thus forming a critical component of effective system administration.
Yes, process auditing in Red Hat Linux indeed involves the examination of process accounting logs to extract useful information. However, it's essential to understand that process auditing and process accounting, while interconnected, are distinct concepts. Process accounting is the mechanism that tracks system usage statistics and activities of each process and command executed in the system. This includes details like CPU usage, memory consumption, command execution times, and the users who initiated these commands. On the other hand, process auditing refers to the systematic review and analysis of these process accounting logs. The primary aims of process auditing are:
- Security Analysis: Auditing enables system administrators to detect any suspicious activity or potential security breaches by analyzing patterns and irregularities in the process accounting logs.
- System Performance Monitoring: By examining the logged data, administrators can identify which processes are resource-intensive, analyze usage patterns, and make necessary adjustments to optimize system performance.
- Troubleshooting and Diagnostics: In case of system issues, auditing the process accounting logs can provide insights into the events leading up to the issue. This data aids in quicker diagnostics and resolution.
- User Accountability: The process accounting logs hold users accountable for their actions on the system. By auditing these logs, administrators can track individual user activities, discouraging misuse and ensuring proper utilization of system resources.
- Forensic Analysis: In case of a security breach, the process accounting logs can serve as a valuable forensic tool. Auditing these logs helps to understand the nature and extent of the intrusion, identify compromised components, and aid in system recovery.
In summary, process auditing in Red Hat Linux involves a thorough analysis of the process accounting logs to retrieve crucial information. This practice enhances system security, optimizes performance, enables efficient troubleshooting, ensures user accountability, and assists in forensic analysis, thus forming a critical component of effective system administration.
What is Process Auditing?
Process auditing refers to examining the process accounting logs and retrieving useful information.
You can use these logs to view the processes that have been executed, the amount of resources the processes used, who executed the processes, and on which machine they were executed. There are built-in utilities that will assist you in retrieving and viewing information on processes.
You can use the
You can use these logs to view the processes that have been executed, the amount of resources the processes used, who executed the processes, and on which machine they were executed. There are built-in utilities that will assist you in retrieving and viewing information on processes.
You can use the
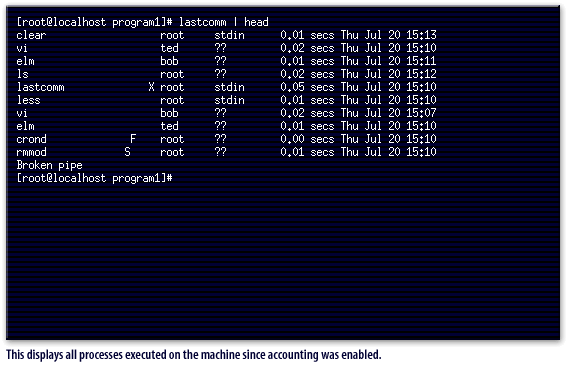
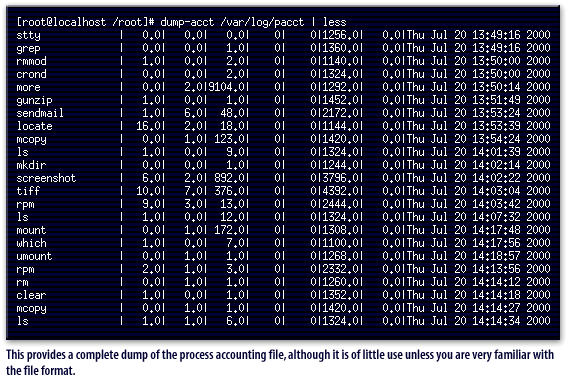
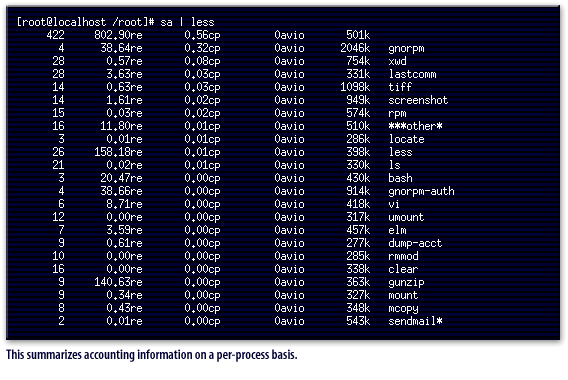
lastcomm command, which examines the logfile /var/log/pacct and displays, in most-recent-first order, all processes executed. This command also has the option to view all processes executed by a specific user, which could be helpful in analyzing exactly what an attacker has done to your machine. The dump-acct provides a complete dump of the process accounting file, although it is of little use unless you are very familiar with the file format. Support is also provided for summarizing resource usage of all executed commands by issuing the sa command, which summarizes accounting information on a per-process basis.
The following series of images below displays examples and output of these commands.
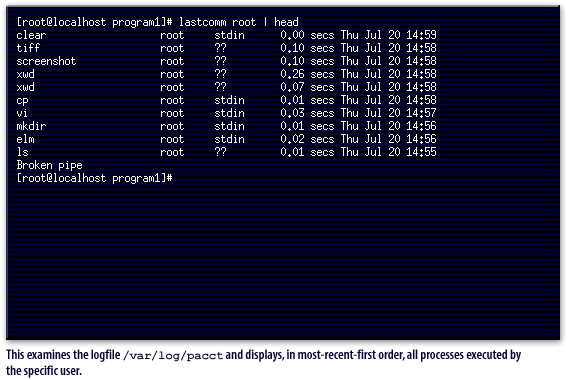
/var/log/pacct and displays, in most-recent-first order, all processes executed by the specific user.
The next lesson describes user auditing.