| Lesson 5 | Setting up shop |
| Objective | Describe how hackers secure a compromised system |
Securing a Compromised System
Hackers often take steps to secure a compromised system in order to maintain persistent access, evade detection, and prevent other attackers from exploiting the same vulnerabilities. The following are some common techniques employed by hackers to secure a compromised system:
Hackers employ various techniques to secure a compromised system and maintain persistent access while evading detection. Understanding these techniques can help security professionals develop strategies to detect, remediate, and prevent such compromises in the future.
- Privilege Escalation: After gaining initial access, hackers may attempt to escalate their privileges to obtain administrative or root access. This allows them greater control over the system, enabling them to manipulate security settings, disable security software, and cover their tracks.
- Installing Backdoors: Hackers may install backdoors on the compromised system to maintain persistent access even if the initial point of entry is closed. Backdoors can take various forms, including remote access tools (RATs), reverse shells, or hidden user accounts with elevated privileges.
- Disabling Security Software: To avoid detection and maintain control, hackers may disable or manipulate security software such as antivirus programs, firewalls, or intrusion detection systems. This can be done by killing security-related processes, modifying configuration files, or injecting malicious code into legitimate processes.
- Log Manipulation: To evade detection, hackers may manipulate or delete system logs that could reveal their activities. This can involve modifying log files to remove traces of their actions, overwriting logs with false information, or configuring the system to stop logging certain events altogether.
- Network Hiding: Hackers may employ techniques to hide their presence on the compromised system's network. This can include using proxy servers or VPNs to obfuscate their true IP address, employing encrypted communication channels to avoid detection, or using domain generation algorithms (DGAs) to generate dynamic command and control (C2) server addresses.
- Rootkits: Hackers may deploy rootkits to hide their presence on a compromised system. Rootkits are sophisticated pieces of malware that operate at the kernel level or below, allowing them to evade detection by many security software solutions. Rootkits can also provide attackers with persistent access and control over the system.
- Patching Vulnerabilities: In order to prevent other attackers from exploiting the same vulnerabilities, hackers may patch the compromised system themselves. This helps to secure their foothold on the system and reduces the likelihood of being discovered by competing malicious actors.
- Lateral Movement: To maintain access to valuable resources within a network, hackers may move laterally to other systems, replicating their actions and securing additional systems. This can involve exploiting vulnerabilities, credential theft, or leveraging misconfigurations to gain access to other devices within the network.
Hackers employ various techniques to secure a compromised system and maintain persistent access while evading detection. Understanding these techniques can help security professionals develop strategies to detect, remediate, and prevent such compromises in the future.
Once crackers enter a system, they operate extremely rapidly. Instructions and executable scripts are available on the Internet to automate the process of securing (from the cracker's perspective) a compromised system. Different operating systems and different installations have different known vulnerabilities,
and these weaknesses are all fully documented. Normally, a cracker will go through a series of steps, which are described below:
Steps to secure System
- The cracker will try to break the
rootaccount, by either obtainingroot's password, or making a program running asrootdo bad things. Withroot, a cracker can do anything! - The log files show all of the activity on the system, so the cracker's
first step after gaining root access is to eliminate them, thereby making themselves invisible. - The cracker then installs a backdoor[1], in case the password on a hacked account is changed. This is accomplished by creating a new user, enabling a normally inactive user, or installing a special server process that allows them to connect again.
- The local password file, if readable, will be retrieved for offline analysis. Exploits of known problems are available for many "secure" networked password systems that allow intruders to also retrieve the password files of other related machines on the network.
- The cracker will try to gain direct access to other machines on the network. For example, if passwords are reused across machines, if users can connect among machines without passwords, or if there are other vulnerable services on the network, the cracker can easily break into additional machines.
Setting up shop and a Compromised System
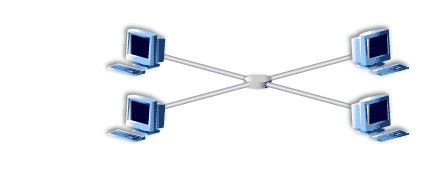
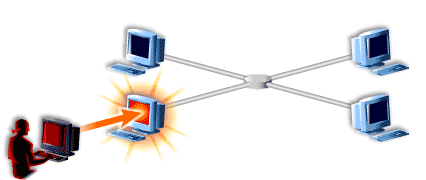
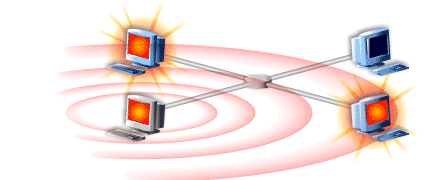
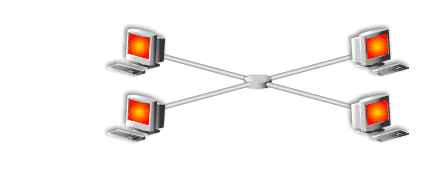
- Here is a network of machines.
- Since security measures have not been implemented, an attacker is able to break into one of the machines.
- An attacker's work is complete since he has compromised one of the machines on the network, so the hacker exits.
- All of the machines have been compromised by the break in, possibly causing irreversible damage due to the malicious software installed on the machine.
Steps Compromised System
The next lesson lists ways that you can detect attacks. Click on the link below to check your understanding of how crackers infiltrate your system.
Common Breakin Procedures
Common Breakin Procedures
[1]Backdoor: A hole placed in you r security by a cracker. It allows the intruder to gain easy access to your system by bypassing normal security.
The following SlideShow shows problems in a compromised system.
The following SlideShow shows problems in a compromised system.