| Lesson 4 | Hackers |
| Objective | How hackers get into a System |
How Hackers get into System
Explain how hackers get into a system.
Hackers are a threat to any machine on the Internet. The explicit purpose of hackers may not be to cause harm to your machine; they might simply be playing around or looking for software to steal. However, hackers will cost you system resources, administration time, and possibly material damage, because once your system has been compromised, you can no longer trust its operability. The following describes some of the various ways hackers gain access to systems.
Hackers are a threat to any machine on the Internet. The explicit purpose of hackers may not be to cause harm to your machine; they might simply be playing around or looking for software to steal. However, hackers will cost you system resources, administration time, and possibly material damage, because once your system has been compromised, you can no longer trust its operability. The following describes some of the various ways hackers gain access to systems.
User oversights
How Hackers retrieve a password from an insecure Public Network
Hackers can employ various techniques to retrieve passwords from insecure public networks. These methods often capitalize on weak security configurations, unencrypted communication, or vulnerabilities in network protocols. The following are some common techniques hackers use to obtain passwords on insecure public networks:
Hackers can employ various techniques to retrieve passwords from insecure public networks, capitalizing on weak security configurations, unencrypted communication, or vulnerabilities in network protocols. Users should be cautious when connecting to public networks and should take measures to protect their sensitive information, such as using strong encryption, enabling two-factor authentication, and being vigilant against phishing attempts.
- Packet Sniffing: Packet sniffing involves capturing and analyzing network data packets transmitted over an insecure public network. When sensitive information, such as passwords, is transmitted without encryption, hackers can intercept these packets and extract the plaintext passwords. Tools like Wireshark or tcpdump are commonly used for packet sniffing.
- Man-in-the-Middle (MITM) Attacks: In MITM attacks, hackers position themselves between the victim and the target server, intercepting and potentially modifying the communication between the two parties. By doing so, attackers can capture login credentials, including passwords, as they are transmitted over the network. Techniques like ARP spoofing or DNS poisoning are often used to facilitate MITM attacks.
- Rogue Access Points: Hackers may set up rogue access points that mimic legitimate public Wi-Fi networks. Unsuspecting users connecting to these malicious access points inadvertently expose their network traffic, including login credentials, to the attacker. This technique is also known as an "Evil Twin" attack.
- Wireless Sniffing: Similar to packet sniffing on wired networks, wireless sniffing involves capturing data packets transmitted over unsecured Wi-Fi networks. Tools like Aircrack-ng or Kismet can be used to intercept and analyze wireless traffic, potentially revealing plaintext passwords.
- Keystroke Logging: Hackers may deploy keystroke logging malware on public computers or devices connected to insecure networks. This malware captures and records the user's keystrokes, including password entries, which are then transmitted back to the attacker.
- Phishing Attacks: Hackers can use phishing attacks to deceive users into revealing their passwords on insecure public networks. This can be achieved by setting up a fake login page that mimics a legitimate service, such as a social media or email platform. Unsuspecting users enter their login credentials, including their passwords, which are then captured by the attacker.
Hackers can employ various techniques to retrieve passwords from insecure public networks, capitalizing on weak security configurations, unencrypted communication, or vulnerabilities in network protocols. Users should be cautious when connecting to public networks and should take measures to protect their sensitive information, such as using strong encryption, enabling two-factor authentication, and being vigilant against phishing attempts.
Sniffing passwords
By far the most common way to retrieve a password is to sniff it from an insecure public network using a password
The sniffer[2] logs all pairs it finds, for the later use of the cracker. If a user ever connects from across the Internet, then his/her password may be compromised in this manner.
The following diagram reviews sniffers in more depth.
The sniffer[2] logs all pairs it finds, for the later use of the cracker. If a user ever connects from across the Internet, then his/her password may be compromised in this manner.
The following diagram reviews sniffers in more depth.
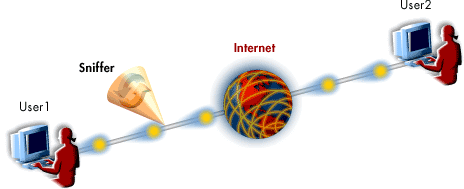
- User 1: has connected to the internet using telnet, an insecure remote service, and is sending packets to User2 via the internet
- Sniffer is copying everything sent between User1 and User2. This is possible because User1 used an insecure remote service
Hackers use Sniffers
The next lesson explains what hackers do once they have broken in.
The next lesson explains what hackers do once they have broken in.
[1]
Social engineering: The use of social techniques, such as masquerading as a system administrator, in order to gain access to confidential user information like a password.
[2]
sniffer: A software password sniffer is a program that looks at all traffic on the network (usually a LAN) for username/password pairs.