| Lesson 5 | IPSec Internet Key Exchange |
| Objective | Define how to negotiate security keys. |
IPSec Internet Key Exchange
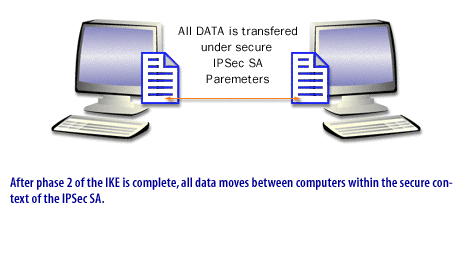
The exchange of authenticated and encrypted data between peers that use IPSec requires negotiation of the security keys.
The negotiation between peers is a two-phase process called Internet Key Exchange. IKE calculates the security keys; using two IETF protocols, the
Internet Security Association and Key Management Protocol (ISAKMP) and the Oakley key generation protocol.
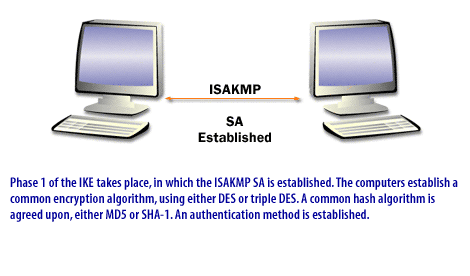
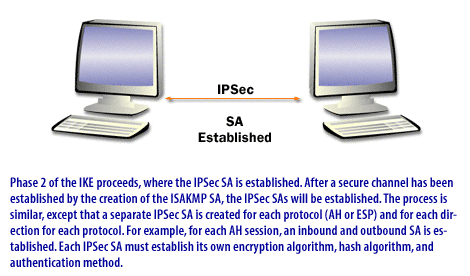
ISAKMP centralizes security association (SA) management, thereby reducing the connection time. Oakley generates and manages the authenticated keys used to secure the information.
- Internet Security Association and Key Management Protocol (ISAKMP): Internet Security Association and Key Management Protocol (ISAKMP) defines a common framework to support the establishment of security associations which are used by IPSec. When combined with the Oakley protocol, it is referred to as the Internet Key Exchange (IKE).
- Oakley key generation protocol: A Key Generation Protocol used to create secure keys for the establishment of a Security Association.
The following Slide Show provides an overview of the IKE.
Internet Key Exchange
Peer authentication methods
IPSec communication between hosts requires that SAs be negotiated between peers. You can use the following peer authentication methods with IPSec:
To find out more IPSec architecture go to the Resources page to view RFC 2401.
The next lesson looks at strategies to enhance the availability of your TCP/IP design.
- The Kerberos 5.0 security protocol: this is the default authentication technology used for any clients running the Kerberos 5.0 protocol that are members of a trusted domain.
- Public key certificates: these are used for authentication between computers that cannot run the Kerberos 5.0 security protocol. Examples of such interaction include Internet access, remote access to corporate resources, and communication with external business partners.
- Preshared keys: this is a shared, secret key, previously agreed upon by two users. Both parties must manually configure IPSec to use this preshared key. This is a simple method for authenticating computers.. Preshared keys are not dependent upon an underlying security infrastructure such as Kerberos or PKI.
To find out more IPSec architecture go to the Resources page to view RFC 2401.
The next lesson looks at strategies to enhance the availability of your TCP/IP design.