| Lesson 4 | Designing Internet and remote access connectivity |
| Objective | Define network services that help manage access to the Internet and support remote users. |
Designing Internet and Remote Access Connectivity
For users on private networks, you will need to design a way to connect them to your network. Connectivity is key to network extensibility.
In the past, most corporate networks lived within the confines of their own network infrastructure. However, the days of the isolated network are over. Companies require real-time processing of information and intelligence, and this requires high-speed connections between networks. To meet these interconnectivity demands, Windows 2000 provides integrated LAN and WAN connectivity services.
Remote Access
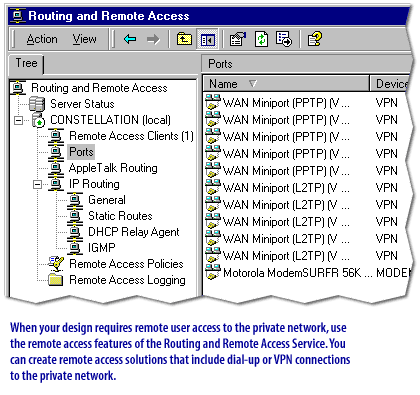
Remote access solutions enable employees to connect to a corporate network from any telephone line in the world. A remote access solution can be implemented by having employees call via a modem band at the home office by dialing an 800 number. A better solution is to take advantage of the Windows 2000 RRAS[1] services Virtual Private Networking (VPN) capabilities. With VPNs[2], remote employees can dial-in to a local Internet Service Provider (ISP) and connect to the corporate network over the Internet. This obviates the cost of direct dial-in solutions via modems.
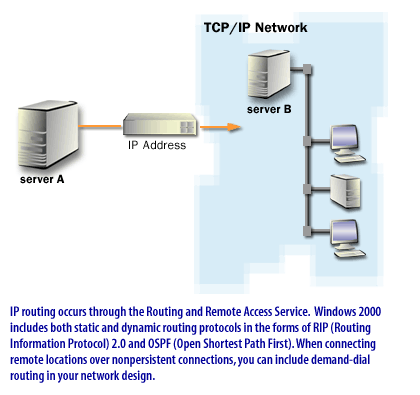
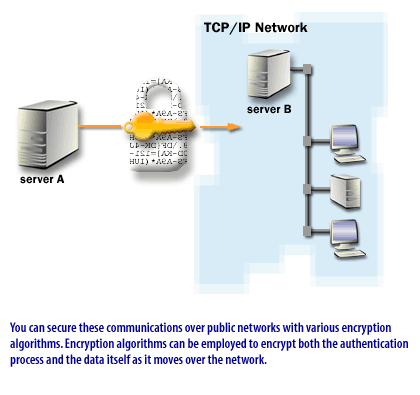
Windows 2000's Internet and Remote Access Service outstrip those available with Windows NT 4.0. VPNs are highly secure, as they take advantage of NAT[3] and L2TP and IPSec technologies. RRAS Clients can also have access controlled via RAS policies, giving the administrator granular control over RAS access to the corporate network. In your network designs, you will include the routing services to connect private networking segments within a geographic location or between locations over public networks, such as the Internet. This will enable remote users to connect to the private network by using authenticated and encrypted connections. The remote-access below describes those routing and remote access features.
Windows 2000's Internet and Remote Access Service outstrip those available with Windows NT 4.0. VPNs are highly secure, as they take advantage of NAT[3] and L2TP and IPSec technologies. RRAS Clients can also have access controlled via RAS policies, giving the administrator granular control over RAS access to the corporate network. In your network designs, you will include the routing services to connect private networking segments within a geographic location or between locations over public networks, such as the Internet. This will enable remote users to connect to the private network by using authenticated and encrypted connections. The remote-access below describes those routing and remote access features.
Define Network Services to manage access to the Internet
Network services that help manage access to the internet and support remote users using DHCP (Dynamic Host Configuration Protocol) involve several key components and functionalities. Here is an overview:
By using DHCP, network administrators can efficiently manage IP address assignments, reduce manual configuration errors, and support both local and remote users with seamless access to network resources. The integration of additional network services like VPN, NAC, and logging further enhances the security and reliability of the network.
- DHCP Server: The DHCP server is a network service that automatically assigns IP addresses and other network configuration parameters to devices (clients) on a network. This simplifies the process of connecting to the internet and ensures efficient IP address management.
- IP Address Allocation: The DHCP server dynamically allocates IP addresses to devices from a predefined range (scope). When a device connects to the network, it sends a DHCP request. The server responds with an available IP address and other necessary network settings.
- Configuration Parameters: In addition to IP addresses, the DHCP server can provide other configuration parameters, such as:
- Subnet Mask: Defines the network and host portions of an IP address.
- Default Gateway: The IP address of the router that forwards traffic to destinations outside the local network.
- DNS Servers: The IP addresses of the servers that resolve domain names to IP addresses.
- Lease Time: The duration for which the IP address is assigned to a device. After the lease expires, the address can be reassigned.
- Remote Access Support: For remote users, network services often include additional features:
- VPN (Virtual Private Network): Establishes a secure connection between the remote user and the corporate network, ensuring data security and privacy over the internet.
- Remote Desktop Services: Allows users to access their office desktop environment from a remote location.
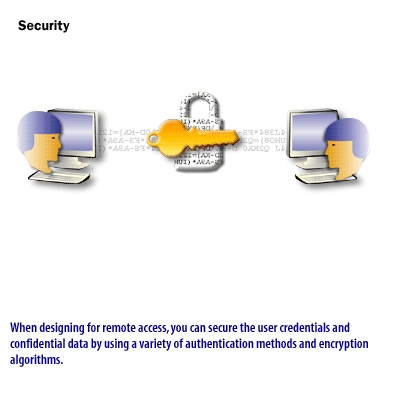
- Authentication Services: Verifies the identity of remote users to ensure secure access to network resources.
- Network Access Control (NAC): NAC solutions integrate with DHCP to enforce security policies and manage access based on the user’s role, device type, and location. It ensures that only authorized devices and users can access the network.
- Logging and Monitoring:
Logging and monitoring tools are essential for tracking DHCP activities, identifying issues, and ensuring network security. These tools can provide insights into:
- DHCP requests and responses
- IP address usage and conflicts
- Unauthorized access attempts
- High Availability and Redundancy: To ensure continuous network access, DHCP servers are often configured in a failover setup, where two or more servers share the load and provide redundancy. If one server fails, the other can continue to provide DHCP services without interruption.
By using DHCP, network administrators can efficiently manage IP address assignments, reduce manual configuration errors, and support both local and remote users with seamless access to network resources. The integration of additional network services like VPN, NAC, and logging further enhances the security and reliability of the network.
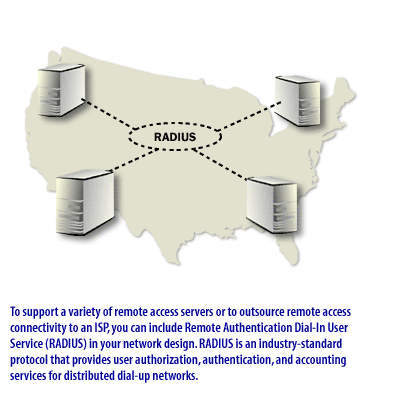
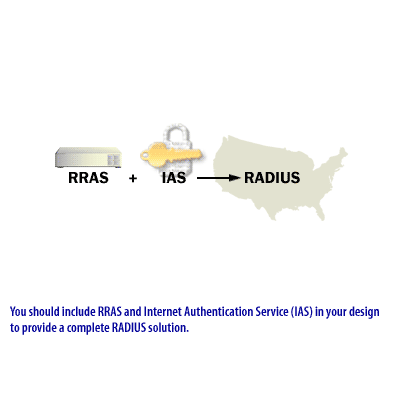
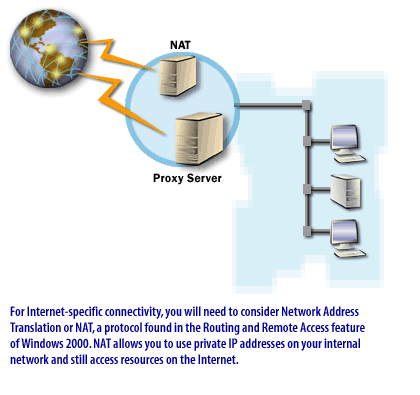
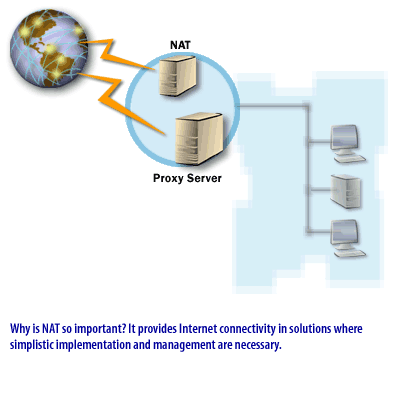
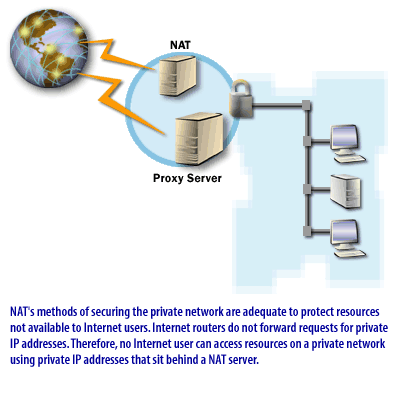
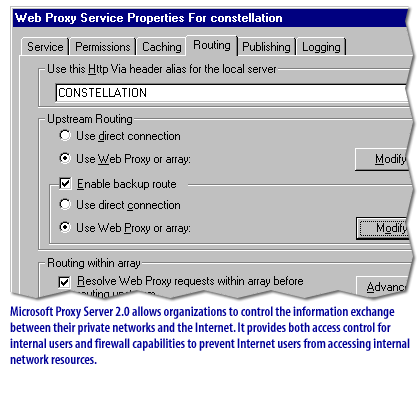
Note that these services are not directed to an organization of any particular size. Your organization may or may not use a service such as NAT.
In the next lesson, you will learn to define tasks involved in creating an integrated networking services design.
[1]
VPNs: Virtual Private Networks. Virtual network connections established over public networks that allow for authentication and encryption of data. VPNs use tunneling technology and private network communications take place inside the encrypted tunnel over the public network.
[2]
NAT: NAT enables private IP addresses to be translated into public IP addresses for traffic to and from the Internet.
[3]
RRAS: The Routing and Remote Access Service. A collection of network services relating to routing and remote access that are brought together into a single Microsoft Management Console.