| Lesson 9 | TCP/IP Solution - Module Conclusion |
| Objective | Review key concepts from Module 3 and assess understanding of TCP/IP design principles, protocol components, and configuration methodologies. |
Module 3 Summary: Designing TCP/IP Solutions
This module provided comprehensive coverage of TCP/IP network design fundamentals, from protocol architecture to practical implementation. You've explored the essential principles, decisions, and methodologies required to design effective, scalable TCP/IP networks for modern enterprise environments.
Module 3 Learning Journey
Lesson 1: Introduction to Designing TCP/IP Solutions
Key Concepts:- Why TCP/IP became the universal networking standard
- Platform independence and scalability advantages
- Fundamental design elements: addressing, routing, services, security
- Critical planning areas for effective TCP/IP deployment
Lesson 2: TCP/IP Protocol Suite Components
Four-Layer Architecture: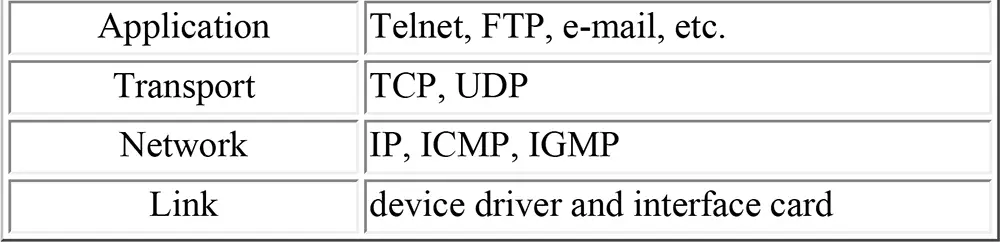
The TCP/IP protocol suite is organized into four functional layers, each with specific responsibilities:
Layer 1 - Network Interface (Link Layer): Handles physical transmission over network media (Ethernet, Wi-Fi). Includes MAC addressing and frame formatting.
Layer 2 - Internet Layer: Provides logical addressing and routing. Core protocols: IP (addressing), ICMP (diagnostics), ARP (address resolution), IGMP (multicast).
Layer 3 - Transport Layer: Enables end-to-end communication. TCP (reliable, connection-oriented) and UDP (fast, connectionless) provide different service levels for applications.
Layer 4 - Application Layer: Delivers network services to applications. Protocols include HTTP/HTTPS, DNS, SMTP, SSH, FTP, DHCP, and SNMP.
Key Protocols:
- IP: Logical addressing and packet routing
- TCP: Reliable, ordered delivery with flow control
- UDP: Fast, lightweight transport for time-sensitive applications
- ICMP: Error reporting and network diagnostics (ping, traceroute)
- ARP: Maps IP addresses to MAC addresses
Lesson 3: Design Decisions for TCP/IP Solutions
Critical Factors:- Host Count: Current and projected device population determines addressing strategy
- Public vs. Private Addressing: Cost, security, and Internet requirements drive choice
- Physical Topology: Subnet count based on WAN links, sites, and network segments
- Infrastructure: Layer 1/2 technologies (Ethernet speeds, wireless standards)
Authentication Architecture:
- Kerberos (preferred for Active Directory)
- LDAPS for directory services
- RADIUS for VPN and network access control
- Modern security: IPsec, TLS 1.3, encryption throughout
Lesson 4: TCP/IP Features and Functionality
Seven Essential Features:- Security: IPsec (AES encryption, SHA-256 authentication), TLS, packet filtering
- QoS (Quality of Service): Bandwidth management, traffic prioritization (DSCP marking)
- APIPA: Automatic private addressing (169.254.0.0/16) for DHCP-less scenarios
- ICMP Router Discovery: Automatic gateway detection
- NetBIOS Management: Disable legacy protocols in modern networks
- TCP Window Scaling: Improves performance over high-bandwidth or high-latency links
- Selective Acknowledgment (SACK): Efficient retransmission during packet loss
Standards Development:
- IETF develops Internet standards through open RFC process
- Vendor-neutral, publicly available specifications
- Community-driven evolution ensures interoperability
Lesson 5: Designing Functional TCP/IP Solutions
IP Addressing Methodologies:| Method | Characteristics | Use Case |
|---|---|---|
| Classful | Fixed masks (Class A/B/C), wasteful, legacy | Obsolete - avoid in new designs |
| CIDR | Flexible prefix lengths (/24, /26, /30) | Modern standard for all networks |
| VLSM | Variable masks within same network | Optimal address utilization |
Routing Protocol Requirements:
- RIPv1: Classful only (obsolete)
- RIPv2, OSPF, EIGRP: Support CIDR and VLSM (modern deployments)
Lesson 6: IP Addressing for Private Networks
RFC 1918 Private Address Ranges:- 10.0.0.0/8: 16.7 million addresses (large enterprises)
- 172.16.0.0/12: 1 million addresses (medium organizations)
- 192.168.0.0/16: 65,536 addresses (small businesses)
Public vs. Private Decision Matrix:
| Factor | Public | Private (RFC 1918) |
|---|---|---|
| Cost | High ($20-50/address) | Free |
| Scalability | Limited by availability | Virtually unlimited |
| Security | Higher exposure | Natural isolation via NAT |
NAT Implementation:
- Static NAT: One-to-one mapping for servers
- Dynamic NAT: Pool of public IPs for outbound connections
- PAT (Overload): Many internal hosts share single public IP (most common)
Hybrid Approach: Most organizations use private addressing internally with NAT, reserving public IPs only for external-facing services (web, mail, VPN).
Lesson 7: IP Address Subnet Requirements
Subnet Design Principles:- Inverse Relationship: More subnet bits = more subnets but fewer hosts per subnet
- Formulas:
- Subnets: 2n (n = borrowed bits)
- Hosts per subnet: 2h - 2 (h = remaining host bits)
Hosts per Subnet Considerations:
- Bandwidth utilization and broadcast domain size
- Router performance limitations
- Application requirements (VoIP, video, databases)
- Future growth projections (reserve 30-50% capacity)
Number of Subnets Required:
- WAN connections (each link needs dedicated subnet)
- Security zones (DMZ, internal, management, guest)
- Departmental segmentation
- Service networks (VoIP, printers, IoT)
- Growth capacity (reserve 50-100% extra subnets)
Practical Examples:
- /26 mask: 4 subnets with 62 hosts each
- /28 mask: 16 subnets with 14 hosts each
- /30 mask: 64 subnets with 2 hosts each (WAN links)
Lesson 8: IP Configuration Methodology
Three Configuration Methods:- Static (Manual) Assignment:
- For: Servers, routers, infrastructure devices
- Benefit: Predictable addressing
- Drawback: Administrative overhead
- DHCP Dynamic Assignment:
- For: Workstations, laptops, mobile devices
- Benefit: Automatic configuration, centralized management
- Drawback: Requires DHCP infrastructure
- DHCP Reservations:
- For: Printers, conference room devices, department servers
- Benefit: Consistent addressing with centralized management
- Drawback: Tied to MAC address (requires update if NIC replaced)
APIPA (Fallback):
- Self-assigns 169.254.x.x address when DHCP unavailable
- Enables basic local connectivity without configuration
- Link-local only (no routing, no Internet access)
- In enterprise: usually indicates DHCP problem requiring troubleshooting
Modern Name Resolution:
- DNS: Primary method for all networks
- mDNS: Zero-configuration for local .local domains
- Legacy (avoid): NetBIOS, WINS (security and performance concerns)
Module Learning Outcomes
Upon completing this module, you should be able to:
- Define TCP/IP protocol suite components and explain the four-layer architecture (Network Interface, Internet, Transport, Application)
- Identify design decisions that influence TCP/IP solutions, including host count, addressing strategy, topology, and infrastructure
- Describe TCP/IP features including security (IPsec), QoS, APIPA, performance enhancements (window scaling, SACK), and diagnostic protocols (ICMP)
- Apply addressing methodologies using CIDR notation, VLSM, and appropriate routing protocols
- Evaluate public versus private addressing schemes and implement NAT for Internet connectivity
- Calculate subnet requirements by determining optimal number of subnets and hosts per subnet based on current needs and growth projections
- Select appropriate configuration methods (static, DHCP, reservations) based on device type and requirements
Key Principles for TCP/IP Design
Performance:
Security:
Scalability:
Operational Excellence:
- Right-size subnets to limit broadcast domains
- Implement QoS for time-sensitive applications
- Monitor bandwidth utilization per segment
- Use TCP window scaling for high-bandwidth or high-latency links
Security:
- Use private addressing with NAT for internal networks
- Implement IPsec for sensitive communications
- Segment networks by security zone (DMZ, internal, management)
- Disable legacy protocols (NetBIOS, LLMNR where not needed)
Scalability:
- Reserve 30-50% capacity for host growth per subnet
- Reserve 50-100% extra subnets for future segmentation
- Use VLSM to optimize address space utilization
- Document addressing scheme in IPAM system
Operational Excellence:
- Use DHCP for clients to reduce configuration errors
- Implement standardized naming conventions
- Maintain comprehensive network documentation
- Plan for IPv6 adoption with dual-stack configuration
The Importance of Proper TCP/IP Design
Well-designed TCP/IP networks deliver:
Consequences of Poor Design:
The investment in thorough TCP/IP design pays dividends for years through improved performance, security, and operational simplicity.
- Optimal Performance: Efficient routing, minimal latency, appropriate QoS
- Enhanced Security: Proper segmentation, isolation of sensitive systems
- Operational Efficiency: Simplified troubleshooting, automated configuration
- Cost Effectiveness: Efficient address utilization, reduced support burden
- Future-Proofing: Capacity for growth without disruptive renumbering
Consequences of Poor Design:
- Network performance degradation (excessive broadcasts, routing inefficiencies)
- Address exhaustion requiring costly renumbering projects
- Security vulnerabilities from inadequate segmentation
- Operational complexity and difficult troubleshooting
- Limited growth capacity
The investment in thorough TCP/IP design pays dividends for years through improved performance, security, and operational simplicity.
TCP/IP: The Foundation of Modern Networking
The TCP/IP protocol suite represents one of the most successful open standards in computing history. What began in the late 1960s as a government-funded research project into packet switching networks has evolved into the universal language of computer networking.
Why TCP/IP Succeeded:
TCP/IP forms the foundation of the global Internet, connecting billions of devices worldwide. Its flexibility, robustness, and extensibility ensure it will remain the dominant networking protocol for the foreseeable future.
Why TCP/IP Succeeded:
- Open Standards: Publicly available specifications developed by IETF
- Vendor Neutral: No single company controls the protocol
- Platform Agnostic: Runs on any operating system and hardware
- Network Independent: Functions over any physical medium
- Scalable: From two devices to billions on the Internet
TCP/IP forms the foundation of the global Internet, connecting billions of devices worldwide. Its flexibility, robustness, and extensibility ensure it will remain the dominant networking protocol for the foreseeable future.
Next Steps
The next module examines securing TCP/IP networks, building on the design fundamentals covered here. Topics include firewall implementation, VPN configuration, intrusion detection, and defense-in-depth security architecture.
Key Terms
- CIDR (Classless Inter-Domain Routing): Flexible IP addressing scheme using prefix lengths (/24, /26) instead of fixed class masks
- VLSM (Variable Length Subnet Masking): Using different subnet masks within the same network for optimal address utilization
- NAT (Network Address Translation): Translates private IP addresses to public addresses, enabling Internet access for private networks
- APIPA (Automatic Private IP Addressing): Self-assignment of 169.254.x.x addresses when DHCP unavailable
- QoS (Quality of Service): Traffic prioritization mechanisms ensuring time-sensitive applications receive adequate bandwidth
- OSI Model: Seven-layer reference model for network protocols developed by ISO (conceptual framework)
- RFC (Request for Comments): Document series containing Internet standards and best practices published by IETF
Assess Your Understanding
Test your comprehension of TCP/IP design principles, protocol components, addressing methodologies, and configuration strategies covered in this module.
TCP/IP Solution - Quiz
Evaluate your mastery of Module 3 concepts including protocol suite architecture, design decisions, subnet calculations, and configuration methodologies.
TCP/IP Solution - Quiz
TCP/IP Solution - Quiz