| Lesson 7 | IP Address Subnet Requirements |
| Objective | Calculate subnet requirements by determining the number of subnets needed and hosts per subnet, then select appropriate subnet masks to meet current and future growth needs. |
Determining IP Address Subnet Requirements
Effective subnet design requires balancing competing demands: enough subnets for network segmentation, sufficient hosts per subnet for each segment's population, and capacity for future growth. Poor subnet planning leads to address exhaustion, costly renumbering projects, or network performance problems. This lesson provides the methodology for calculating subnet requirements and selecting appropriate subnet masks.
The Subnet Design Challenge
Subnet mask selection involves an inverse relationship between the number of subnets and hosts per subnet:
Design Constraints:
Goal: Select a subnet mask that accommodates current requirements while providing headroom for growth in both dimensions.
- More subnet bits = More subnets, Fewer hosts per subnet
- Fewer subnet bits = Fewer subnets, More hosts per subnet
Design Constraints:
- Physical Subnets: Number of actual network segments (VLANs, remote sites, WAN links)
- Logical Subnets: Additional segmentation for security zones, departments, or services
- Host Population: Number of devices required on each subnet
- Growth Projections: Expected expansion over 3-5 years
- Router Limitations: Maximum hosts supported per interface
Goal: Select a subnet mask that accommodates current requirements while providing headroom for growth in both dimensions.
Subnet Mathematics Fundamentals
Understanding the relationship between borrowed bits, subnets created, and hosts available is essential for subnet planning.
Key Formulas:
Key Formulas:
- Number of Subnets: 2n where n = bits borrowed from host portion
- Hosts per Subnet: 2h - 2 where h = remaining host bits
- Subtract 2 for network address (all zeros) and broadcast address (all ones)
Subnetting a Class C Network: Visual Examples
The following examples demonstrate how borrowing different numbers of bits affects subnet count and host capacity using a Class C network (192.168.1.0/24).
Example 1: No Subnetting (Default Class C)
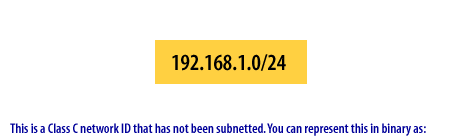
Network: 192.168.1.0/24
Binary Representation:
IP Address: 11000000.10101000.00000001.00000000 (192.168.1.0)
Subnet Mask: 11111111.11111111.11111111.00000000 (255.255.255.0)
Result:
- Subnets: 1 (no division)
- Hosts per subnet: 254 (28 - 2)
- Network address: 192.168.1.0
- Broadcast address: 192.168.1.255
- Usable range: 192.168.1.1 - 192.168.1.254
The mask bits (1s) define the network portion; the host bits (0s) define the host portion. With default mask, entire last octet available for host addresses.
Example 2: Borrowing 2 Bits (/26 Mask)
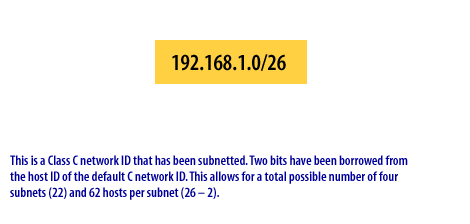
Network: 192.168.1.0/26
Subnet Mask: 255.255.255.192
Binary: 11111111.11111111.11111111.11000000
Calculation:
- Bits borrowed: 2
- Subnets created: 22 = 4 subnets
- Remaining host bits: 6
- Hosts per subnet: 26 - 2 = 62 hosts
Four Subnets:
| Subnet | Network Address | Usable Range | Broadcast |
|---|---|---|---|
| 1 | 192.168.1.0 | 192.168.1.1 - 62 | 192.168.1.63 |
| 2 | 192.168.1.64 | 192.168.1.65 - 126 | 192.168.1.127 |
| 3 | 192.168.1.128 | 192.168.1.129 - 190 | 192.168.1.191 |
| 4 | 192.168.1.192 | 192.168.1.193 - 254 | 192.168.1.255 |
Use Case: Small office with 4 departments, each with up to 62 devices.
Example 3: Borrowing 4 Bits (/28 Mask)
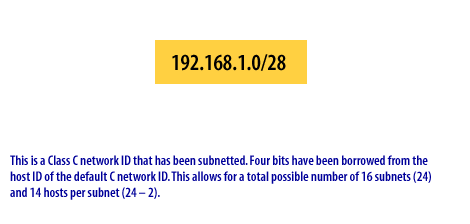
Network: 192.168.1.0/28
Subnet Mask: 255.255.255.240
Binary: 11111111.11111111.11111111.11110000
Calculation:
- Bits borrowed: 4
- Subnets created: 24 = 16 subnets
- Remaining host bits: 4
- Hosts per subnet: 24 - 2 = 14 hosts
Sample Subnets:
| Subnet | Network Address | Usable Range | Broadcast |
|---|---|---|---|
| 1 | 192.168.1.0 | 192.168.1.1 - 14 | 192.168.1.15 |
| 2 | 192.168.1.16 | 192.168.1.17 - 30 | 192.168.1.31 |
| 3 | 192.168.1.32 | 192.168.1.33 - 46 | 192.168.1.47 |
| ... | ... | ... | ... |
| 16 | 192.168.1.240 | 192.168.1.241 - 254 | 192.168.1.255 |
Use Case: Network with many small segments (conference rooms, small branch offices, point-to-point links) each requiring 10-14 devices.
Subnet Selection Quick Reference
| Bits Borrowed | CIDR | Subnet Mask | Subnets | Hosts/Subnet | Use Case |
|---|---|---|---|---|---|
| 0 | /24 | 255.255.255.0 | 1 | 254 | Single large network |
| 1 | /25 | 255.255.255.128 | 2 | 126 | Split into two large segments |
| 2 | /26 | 255.255.255.192 | 4 | 62 | Medium departments |
| 3 | /27 | 255.255.255.224 | 8 | 30 | Small departments |
| 4 | /28 | 255.255.255.240 | 16 | 14 | Very small segments |
| 5 | /29 | 255.255.255.248 | 32 | 6 | Micro segments |
| 6 | /30 | 255.255.255.252 | 64 | 2 | Point-to-point WAN links |
Determining Hosts per Subnet Requirements
Several factors influence how many hosts should be placed on each subnet:
Broadcast Domain Size:
Collision Domain Considerations:
1. Performance Considerations
Bandwidth Utilization:- Monitor actual network utilization per segment (not aggregate)
- Target: Keep utilization below 40-50% sustained, 70% peak
- Tools: Windows Performance Monitor, PRTG, MRTG, SolarWinds
- High-bandwidth applications (VoIP, video, CAD) may require dedicated subnets
Broadcast Domain Size:
- All devices on subnet receive all broadcasts
- Too many hosts = excessive broadcast traffic
- Recommended maximum: 250-500 hosts per subnet (depending on application profile)
- Windows networks generate broadcasts for: ARP, NetBIOS (if enabled), DHCP, multicast discovery
Collision Domain Considerations:
- Modern switched networks eliminate collisions (full-duplex)
- Legacy hubs create collision domains (avoid in new deployments)
- Switches segment collision domains to individual ports
2. Router Performance Limits
- Check router specifications for maximum hosts per interface
- Small office routers: Typically 250-500 hosts
- Enterprise routers: Thousands to tens of thousands
- Performance degradation factors:
- ARP table size limits
- Routing table processing
- ACL processing overhead
- NAT connection tracking (if applicable)
3. Application Requirements
Test with Production Applications:- Lab testing may not reflect real-world behavior
- Simulate actual user loads and traffic patterns
- Measure: Throughput, latency, packet loss, jitter (for VoIP/video)
- Application-specific considerations:
- Database applications: Low latency critical, moderate bandwidth
- VoIP: <150ms latency, <1% loss, <30ms jitter
- Video conferencing: 1-5 Mbps per stream, low latency
- File servers: High bandwidth, latency less critical
4. Future Growth Planning
- Analyze historical growth trends (3-5 year lookback)
- Factor in business expansion plans (new hires, acquisitions, office moves)
- Reserve 30-50% capacity for growth
- Example: If current needs = 40 hosts, plan for subnet supporting 60-70
- Easier to oversize subnets initially than renumber later
Determining Number of Subnets Required
1. Physical Network Topology
WAN Connections:- Each point-to-point WAN link requires dedicated subnet
- Use /30 mask (2 hosts) for router-to-router links
- Example: 10 branch offices = minimum 10 WAN subnets
Physical Sites:
- Each physical location typically requires at least one subnet
- Large sites may need multiple subnets (one per floor/building)
2. Logical Network Segmentation
Security Zones:- DMZ (public-facing servers): Dedicated subnet(s)
- Internal servers: Separate from user workstations
- Management network: Isolated subnet for infrastructure management (switches, firewalls, iLO/iDRAC)
- Guest network: Isolated from corporate resources
Departmental Segmentation:
- Separate subnets for different departments (HR, Finance, Engineering)
- Enables granular access control via firewall rules or ACLs
- Limits broadcast domains
Service Networks:
- VoIP phones: Dedicated voice VLAN
- Printers/scanners: Separate management subnet
- IoT devices: Isolated from business network
- Building automation: Separate OT (operational technology) network
3. Overloaded Segments
- If a subnet exceeds router capacity, split into multiple subnets
- Formula: Required routers at location = Total hosts ÷ Hosts supported per router
- Example: 1,000 hosts, router supports 250 per interface = Need 4 subnets minimum
4. Growth Planning for Subnets
- Err on side of excess subnets: Easier to leave subnets unused than run out
- Reserve 50-100% extra subnet capacity
- Example: Currently need 8 subnets → Choose mask providing 16
- Rationale: Router technology limits hosts/subnet, but creating new subnets is straightforward if address space allows
Bandwidth Monitoring Best Practices
Effective bandwidth monitoring informs subnet sizing decisions and identifies performance bottlenecks.
Why Aggregation Misleads:
Proper Approach:
High-Bandwidth Applications:
Per-Segment Monitoring
Critical Principle: Monitor each network segment individually, not aggregate statistics.Why Aggregation Misleads:
- Example: 10 segments with 9 at 10% utilization, 1 at 95% utilization
- Aggregate average: 18.5% (appears healthy)
- Reality: One segment severely overloaded, causing user complaints
- Aggregate numbers hide problems and inflate healthy segment stats
Proper Approach:
- Monitor each subnet/VLAN separately
- Set alerts on per-segment thresholds (e.g., >70% sustained)
- Track trends over time to identify growing congestion
- Proactive monitoring prevents problems before users affected
Application-Specific Bandwidth Planning
Pre-Deployment Testing:- Measure baseline utilization on current segments
- Lab-test new application with simulated user loads
- Project bandwidth increase: Baseline + Application demand
- Compare to available capacity
- If capacity inadequate, options:
- Upgrade link speed (100 Mbps → 1 Gbps)
- Segment users across multiple subnets
- Implement QoS to prioritize critical traffic
- Schedule bulk transfers during off-peak hours
High-Bandwidth Applications:
| Application Type | Bandwidth per User | Consideration |
|---|---|---|
| VoIP | 80-100 Kbps | Latency-sensitive, requires QoS |
| Video Conferencing | 1-5 Mbps | Variable quality settings |
| CAD/Graphics | Variable (large files) | Burst traffic, benefit from 10 Gbps server |
| Database Queries | Moderate | Latency more critical than bandwidth |
Subnet Design Methodology
Step-by-Step Process:
- Inventory Requirements
- Count current hosts per location/department
- Identify required network segments (physical + logical)
- Document application bandwidth requirements
- Project Growth
- Estimate host count increase over 3-5 years
- Plan for new sites/departments
- Factor in technology changes (IoT, BYOD)
- Calculate Requirements
- Hosts per subnet = Current maximum + 30-50% growth
- Number of subnets = Physical segments + Logical segments + 50-100% growth
- Select Subnet Mask
- Find mask providing sufficient subnets AND hosts per subnet
- Use VLSM if segments have dramatically different sizes
- Document decisions and reasoning
- Allocate Address Space
- Assign specific subnet ranges to each segment
- Maintain hierarchical structure for route summarization
- Reserve blocks for future expansion
- Test and Validate
- Lab testing of routing configuration
- Verify ACLs and firewall rules
- Pilot deployment before full rollout
Benefits of Proper Subnetting
- Increased Network Capacity: Dividing into subnets reduces per-segment host count, decreasing congestion
- Improved Performance: Smaller broadcast domains mean less broadcast traffic
- Enhanced Security: Firewall rules between subnets control inter-segment access
- Customized Topology: Network structure reflects organizational structure
- Efficient Address Management: Right-size subnets minimize waste while accommodating growth
- Flexible Growth: Proper planning prevents address exhaustion
Trade-off: Subnetting increases complexity (routing configuration, ACL management, documentation requirements), but benefits far outweigh costs for networks beyond the simplest deployments.
Practical Application
Apply subnet calculation skills to real-world scenarios involving subnet count determination, host capacity planning, and mask selection.
IP Address Subnet Requirements - Exercise
Practice calculating subnet requirements, determining appropriate masks, and allocating address space for various network designs.
IP Address Subnet Requirements - Exercise
IP Address Subnet Requirements - Exercise