Internet Key Exchange
The management of keying material for IPsec security associations (SAs) is called key management. Automatic key management requires a secure channel of communication for the creation, authentication, and exchange of keys.
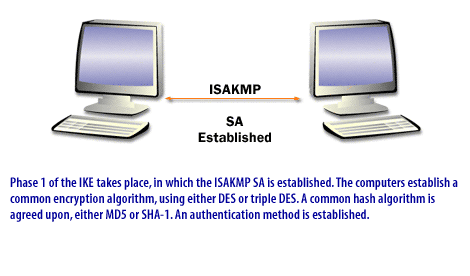
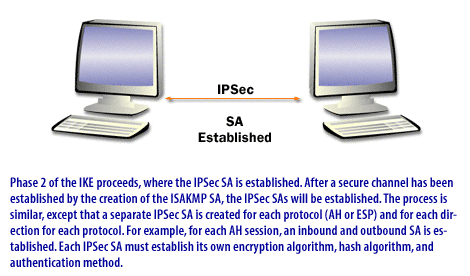
Oracle Solaris uses Internet Key Exchange (IKE) to automate key management. IKE eliminates administrative overhead and the security risk of manually distributing secret keys. IKE can take advantage of available hardware cryptographic acceleration and key storage.
Hardware cryptographic accelerators permit CPU-intensive key operations to be handled off the system.
Key storage on hardware provides an additional layer of protection.
Oracle Solaris supports two versions of the IKE protocol.
- IKE Version 2 (IKEv2), which is based on Internet Key Exchange Protocol Version 2 (IKEv2), RFC 5996
- IKE Version 1 (IKEv1), which is based on The Internet Key Exchange (IKE), RFC 2409
DHCP Knowledge