| Lesson 5 | Configuring an interface in Linux |
| Objective | Examine output of dmesg command/identify network devices |
Configuring Linux Network Interface
Examine output of dmesg command to identify network devices
Examine the output of the dmesg command to identify the network devices attached to the system. Now that you have seen how to set up name service, we will return to the more fundamental problems of configuring an interface with its IP address and netmask.[1] As you have learned, the kernel probes the hardware during the boot process. During this probing, the kernel will recognize the network devices attached to the system and report on them. The results of this hardware probe are available from the
Examine the output of the dmesg command to identify the network devices attached to the system. Now that you have seen how to set up name service, we will return to the more fundamental problems of configuring an interface with its IP address and netmask.[1] As you have learned, the kernel probes the hardware during the boot process. During this probing, the kernel will recognize the network devices attached to the system and report on them. The results of this hardware probe are available from the
dmesg command.
Linux Kernels without Network Support
Almost all modern Linux kernels have networking capabilities compiled into the kernel by default.
This means they come with the necessary drivers and modules to manage and utilize network interfaces like wired and wireless connections.
There might be some "rare and specific cases" where networking support is not included:
Overall, for most modern Linux distributions and kernels used on desktops, servers, and various devices, networking functionality is an essential and included feature. For further confirmation, you can check the specific kernel version you are using. There are two ways to do this:
Very old Linux kernels or non-standard packages, may not have networking compiled into the kernel. However, these circumstances are nonexistent as of February 2024 and there is no reason to compile a Linux kernel which does not have network support. In this case, the kernel will not detect ethernet devices or other network interfaces. You must rebuild the kernel (or obtain a newer release) to use networking. Nowadays, it is hard to imagine a Linux kernel that does not provide network support.
- Custom-built kernels for embedded systems or specialized devices: These may have limited functionality and exclude unnecessary components like networking for resource optimization.
- Security-focused kernels: In very specific security-oriented deployments, networking might be intentionally disabled to reduce attack surface. However, this is not a common scenario for general-purpose Linux distributions.
Overall, for most modern Linux distributions and kernels used on desktops, servers, and various devices, networking functionality is an essential and included feature. For further confirmation, you can check the specific kernel version you are using. There are two ways to do this:
- Command line: Run `uname -r` in your terminal. This will display the kernel version.
- Distribution information: If you are using a specific Linux distribution, you can refer to its documentation or community resources to confirm if networking is included by default for the kernel version used.
Very old Linux kernels or non-standard packages, may not have networking compiled into the kernel. However, these circumstances are nonexistent as of February 2024 and there is no reason to compile a Linux kernel which does not have network support. In this case, the kernel will not detect ethernet devices or other network interfaces. You must rebuild the kernel (or obtain a newer release) to use networking. Nowadays, it is hard to imagine a Linux kernel that does not provide network support.
Overview of Operating Systems and Kernels
Because of the ever-growing feature set and ill design of some modern commercial operating systems, the notion of what precisely defines an operating system is not universal. Many users consider whatever they see on the screen to be the operating system. Technically speaking, and in this book, the operating system is considered the parts of the system responsible for basic use and administration. This includes the kernel and device drivers, boot loader, command shell or other user interface, and basic file and system utilities. It is the stuff you need, not a web browser or music players. The term system refers to the operating system and all the applications running on top of it. Of course, the topic of this book is the kernel. Whereas the user interface is the outermost portion of the operating system, the kernel is the innermost. It is the core internals; the software that provides basic services for all other parts of the system, manages hardware, and distributes system resources.
The kernel is sometimes referred to as the supervisor, core, or internals of the operating system.Typical components of a kernel are interrupt handlers to service interrupt requests, a scheduler to share processor time among multiple processes, a memory management system to manage process address spaces, and system services such as networking and interprocess communication.
The kernel is sometimes referred to as the supervisor, core, or internals of the operating system.Typical components of a kernel are interrupt handlers to service interrupt requests, a scheduler to share processor time among multiple processes, a memory management system to manage process address spaces, and system services such as networking and interprocess communication.
Kernel Space
On modern systems with protected memory management units, the kernel typically resides in an elevated system state compared to normal user applications. This includes a protected memory space and full access to the hardware. This system state and memory space is collectively referred to as kernel-space. Conversely, user applications execute in user-space. They see a subset of the machine's available resources and can perform certain system functions, directly access hardware, access memory outside of that allotted them by the kernel, or otherwise misbehave. When executing kernel code, the system is in kernel-space executing in kernel mode. When running a regular process, the system is in user-space executing in user mode. Applications running on the system communicate with the kernel via system calls. An application typically calls functions in a library. For example, the C library, which relies on the system call interface to instruct the kernel to carry out tasks on the application's behalf.
Some library calls provide many features not found in the system call, and thus, calling into the kernel is just one step in an otherwise large function. For example, consider the familiar
Some library calls provide many features not found in the system call, and thus, calling into the kernel is just one step in an otherwise large function. For example, consider the familiar
printf() function. It provides formatting and buffering of the data; only one step in its work is invoking write() to write the data to the console. Conversely, some library calls have a one-to-one relationship with the kernel. For example, the open() library function does little except call the open() system call. Still other C library functions, such as strcpy(), should (one hopes) make no direct use of the kernel at all.When an application executes a system call, we say that the kernel is executing on behalf of the application. Furthermore, the application is said to be executing a system call in kernel-space, and the kernel is running in process context. This relationship, that applications call into the kernel via the system call interface is the fundamental manner in which applications get work done.
This Particular ethernet interface is eth0
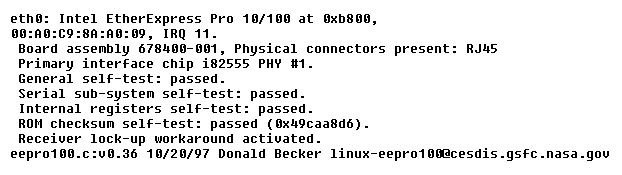
- This particular ethernet interface is eth0. Later references to it will be through that name.
- Every ethernet card is shipped with a hard-wired ethernet address. This address is 48 bits long, and is usually written as six colon-separated sets of two-digit hexadecimal numbers. In this example, the ethernet address is 00:A0:C9:8A:A0:09.
Click the link to examine the following output, which describes an Intel EtherExpress card identified by the kernel.
dmesg command output
Not all UNIX systems are this informative about installed devices.
Later, during our discussion of the
This output means that the PPP[2] link-layer protocol is installed in the kernel, and that a PPP device (ppp0) is available. On a Linux machine, such as the one from which this output was taken, the PPP kernel code is part of a loadable kernel module. This module is installed only when needed, such as when a PPP phone connection starts. Therefore, this message may not always appear, even when PPP is available.
Later, during our discussion of the
ifconfig command, we will see another way to determine the ethernet address (or other link-layer addresses) for network devices. Here is another example of kernel output relevant to network devices:
PPP: version 2.2.0 (dynamic channel allocation)
PPP Dynamic channel allocation code
copyright 1995 Caldera, Inc.
PPP line discipline registered.
registered device ppp0
This output means that the PPP[2] link-layer protocol is installed in the kernel, and that a PPP device (ppp0) is available. On a Linux machine, such as the one from which this output was taken, the PPP kernel code is part of a loadable kernel module. This module is installed only when needed, such as when a PPP phone connection starts. Therefore, this message may not always appear, even when PPP is available.
[1]
Netmask: A 32-bit bit mask which shows how an Internet address is to be divided into network, subnet and host parts.
[2]
Point-to-point protocol (PPP): A protocol for connecting to the Internet. PPP provides error checking and compression of the IP and TCP headers.