The Application Layer of the TCP/IP Protocol
| Lesson 3 | The application layer of the TCP-IP Protocol |
| Objective | What is the application layer of the TCP-IP Protocol? |
The Application Layer is the topmost layer of the TCP/IP model and serves as the interface between network services and end users. It defines how applications interact across networks and determines the “language” used by clients and servers to exchange data. Whether it’s loading a webpage, sending an email, or establishing a secure connection, all such tasks begin here.
Purpose and Function
In the TCP/IP stack, the Application Layer provides protocols and services that enable direct communication between software applications over the Internet or a local network. While lower layers handle data transmission, routing, and transport reliability, the Application Layer focuses on content, format, and user interaction. It allows applications to access network resources without needing to manage the underlying mechanics of connectivity.
Core Components of the Application Layer
-
Application Protocols
These define the rules for specific types of network communication. Common examples include:HTTP– Transfers web content between clients and servers. The foundation of the World Wide Web.HTTPS– A secure version of HTTP usingTLSencryption to protect transmitted data.SFTPandFTPS– Secure alternatives to traditional FTP, using SSH or TLS to protect credentials and data in transit.SMTP– Sends email between mail servers, often combined with authentication and encryption standards like STARTTLS.DNS– Resolves human-readable domain names into IP addresses.POP3andIMAP– Retrieve and manage email from remote servers. IMAP allows synchronization across devices; POP3 typically downloads messages locally.SSH– Provides encrypted remote access to systems, replacing insecure methods like Telnet.
-
Network Services
These are specialized programs that provide shared access to network resources:- Web Services: Host and deliver web pages (e.g., Apache, Nginx).
- File Services: Manage file sharing using SFTP or SMB.
- Directory and Naming Services: Manage user authentication and name resolution (e.g., LDAP, DNS).
- Email Services: Handle mail delivery and retrieval (e.g., Postfix, Dovecot).
-
Interfaces and APIs
Application Programming Interfaces (APIs) enable software developers to build networked applications without managing low-level socket communication. APIs such asPOSIX sockets,libcurl, and Java’sHttpClientabstract away transport details while ensuring standards-based connectivity. -
Client and Server Software
These are implementations of the Application Layer protocols. Examples include:- Web Clients: Google Chrome, Mozilla Firefox.
- Web Servers: Apache, Nginx.
- Email Clients: Thunderbird, Outlook.
- Email Servers: Postfix, Exchange Server.
- Secure Shell Services: OpenSSH.
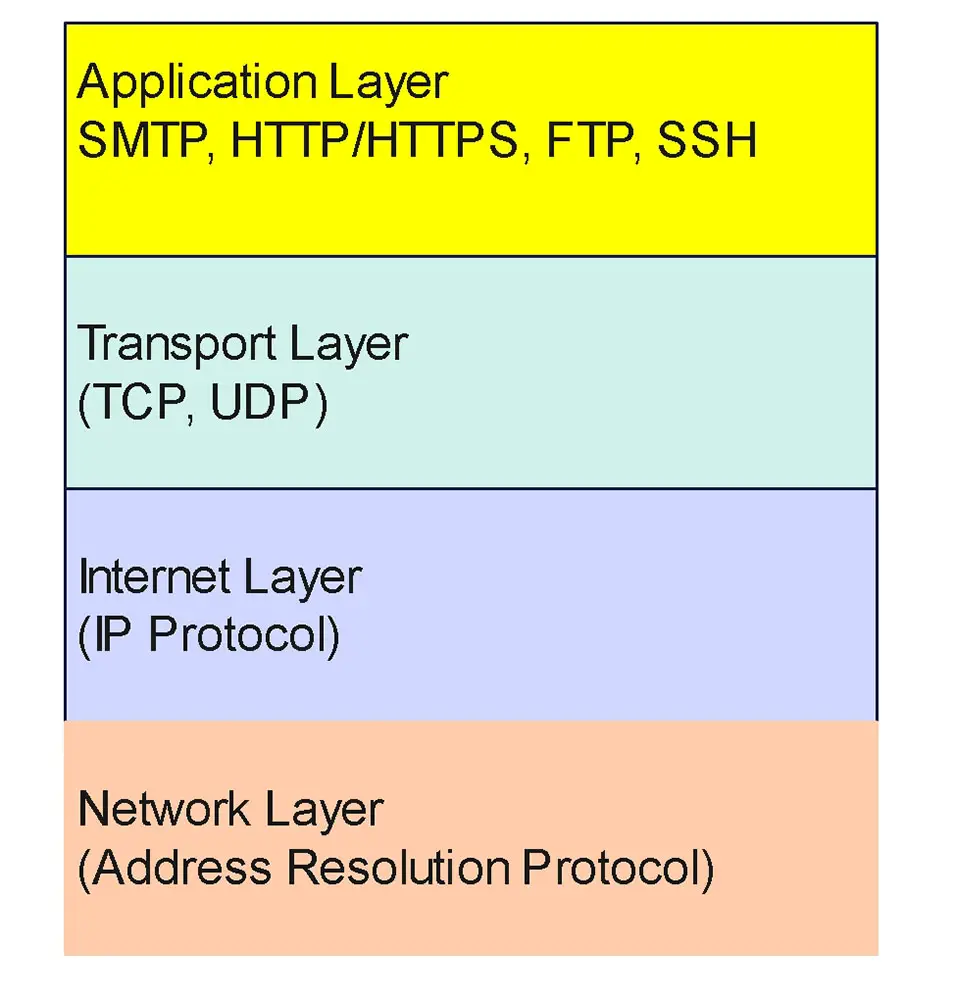
Application-Layer Protocols in Context
Application-layer protocols rely on the lower layers of the TCP/IP model—Transport, Internet, and Link—for delivery and addressing. On UNIX and Linux systems, these lower layers are handled by the kernel, allowing application software to focus solely on data structure and content.
Typical examples of application-layer protocols include:
HTTP– Web page retrievalSMTP– Email transferDNS– Domain resolutionDHCP– Dynamic IP address assignment
How Application Data Travels
Data from the Application Layer is encapsulated by the Transport Layer into segments (TCP) or datagrams (UDP), which are then passed to the Internet Layer for routing and the Link Layer for transmission. The Application Layer itself does not concern itself with delivery mechanics—it assumes a reliable connection provided by lower layers.
Application protocols typically use well-known port numbers managed by IANA. For example:
- HTTP → Port 80
- HTTPS → Port 443
- SMTP → Port 25
- SSH → Port 22
Clients, on the other hand, use ephemeral ports—temporary numbers assigned for each session. This client-server model allows thousands of simultaneous connections across the Internet without interference.
Security Considerations
Modern best practices discourage the use of legacy, unencrypted protocols such as TELNET or plain FTP. These protocols transmit data, including credentials, in clear text and are susceptible to interception. Always use secure variants:
- SFTP or FTPS instead of FTP
- SSH instead of Telnet
- HTTPS instead of HTTP for sensitive data
For encryption and authentication, use modern cryptographic standards such as AES (Advanced Encryption Standard) and SHA-256 hashing instead of outdated algorithms like DES.
Summary
The Application Layer bridges human interaction and machine communication. It defines how user-facing software exchanges data across a network while abstracting the complexity of lower-level networking. By following modern standards for encryption and protocol design, administrators and developers can ensure that their applications remain secure, interoperable, and efficient.
TCP-IP Layers Application - Quiz
TCP-IP Layers Application - Quiz