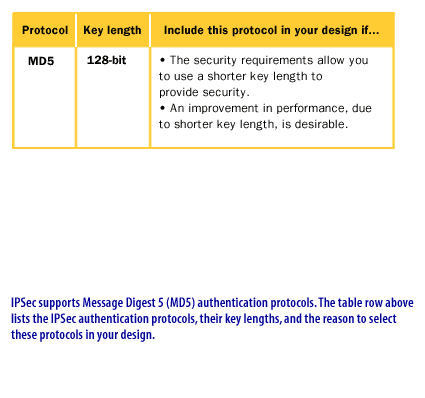
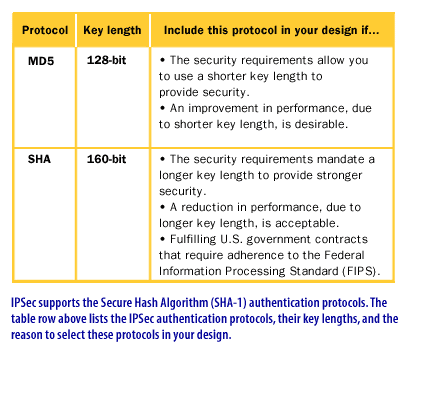
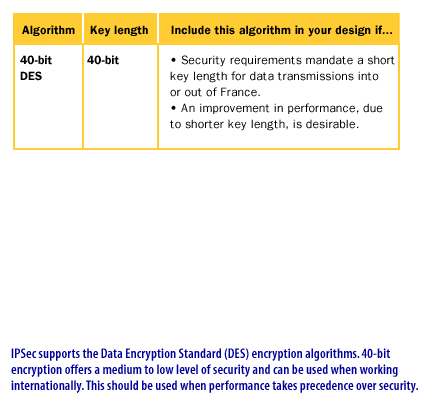
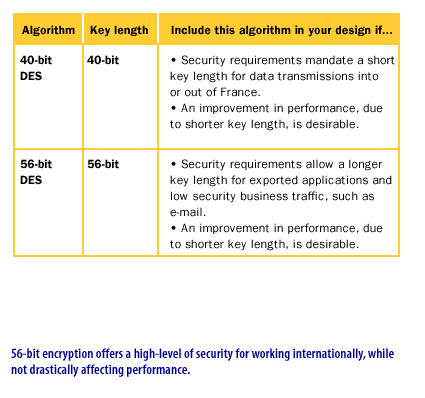
IPSec Protection Protocols
IPsec provides two security protocols for protecting data:
AH provides data integrity by using an authentication algorithm. It does not encrypt the packet. ESP typically protects the packet with an encryption algorithm and provides data integrity with an authentication algorithm. Some encryption algorithms provide both encryption and authentication, such as AES GCM. The AH protocol cannot be used with network address translation (NAT).
- Authentication Header (AH)
- Encapsulating Security Payload (ESP)
AH provides data integrity by using an authentication algorithm. It does not encrypt the packet. ESP typically protects the packet with an encryption algorithm and provides data integrity with an authentication algorithm. Some encryption algorithms provide both encryption and authentication, such as AES GCM. The AH protocol cannot be used with network address translation (NAT).