| Lesson 3 | Determining the number of screened subnets |
| Objective | Define the number of screened subnets required in the Internet connectivity design. |
Determine number of Screened Subnets
One way to restrict access to the Internet is by preventing traffic from passing through the proxy server. This can be done in a variety of ways. In this lesson, we will focus our discussion on the first of these methods which is establishing screened subnets. If you find the term "screened subnets" confusing, you are not alone. A check of the latest Microsoft®
TechNet reveals a single entry that mentions the term in a single instance. However, this term is in widespread use in the general networking community, and has been introduced for just about the first time in the Windows 2000 curriculum.
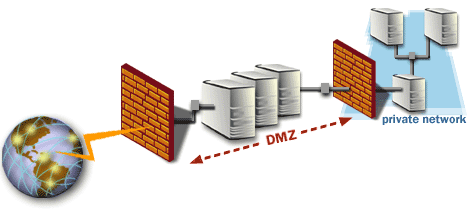
The DMZ
The term more commonly used for screened subnet is a Demilitarized Zone or DMZ. A DMZ subnet is used to place resources that are accessible to Internet users. This reduces the risk to internal network servers because Internet users do not access resources on the internal network, but rather only the DMZ network. The classic example of a DMZ is a subnet placed between the Internet and the internal network. Internet accessible resources are placed on the DMZ subnet,
and customized access controls are configured on the edge firewall and the internal firewall.
Multihomed Proxy Server
A demilitarized zone (DMZ) can be created by using a multihomed proxy server. A DMZ is a specific type of network segmentation that acts as an additional layer of security between an organization's local area network (LAN) and the public Internet.
In the context of network security, a multihomed device is one that has multiple network interfaces, each connected to a different network or network segment. A multihomed proxy server is a server that has at least two network interfaces and acts as an intermediary for requests from clients seeking resources from other servers.
Here is how a multihomed proxy server can create a DMZ:
In this setup, the network segment that contains the proxy server forms the DMZ. The proxy server intercepts traffic coming from both the LAN and the Internet, effectively isolating the two networks from direct contact with each other.
Because the proxy server is the only device that communicates directly with the Internet, it can be fortified with extra security measures such as packet filtering, intrusion detection systems, and application-level gateways. This provides an additional layer of protection for the LAN by shielding it from direct exposure to the Internet. In summary, a multihomed proxy server can be effectively used to create a DMZ, enhancing the security posture of an organization by adding a buffer zone that helps protect the internal network from external threats.
In the context of network security, a multihomed device is one that has multiple network interfaces, each connected to a different network or network segment. A multihomed proxy server is a server that has at least two network interfaces and acts as an intermediary for requests from clients seeking resources from other servers.
Here is how a multihomed proxy server can create a DMZ:
- One network interface of the proxy server is connected to the internal network (LAN).
- Another network interface is connected to the external network, typically the Internet.
- The proxy server is configured to forward requests from the internal network to the external network and vice versa.
In this setup, the network segment that contains the proxy server forms the DMZ. The proxy server intercepts traffic coming from both the LAN and the Internet, effectively isolating the two networks from direct contact with each other.
Because the proxy server is the only device that communicates directly with the Internet, it can be fortified with extra security measures such as packet filtering, intrusion detection systems, and application-level gateways. This provides an additional layer of protection for the LAN by shielding it from direct exposure to the Internet. In summary, a multihomed proxy server can be effectively used to create a DMZ, enhancing the security posture of an organization by adding a buffer zone that helps protect the internal network from external threats.
When using a Proxy Server with multiple adapters, you configure packet filtering and access controls in a fashion similar to the firewall configuration. In this case, however, Proxy Server 2.0 acts as both the firewall and a router. Internet requests are routed to the DMZ while all requests from the Internet made to the internal network are dropped by the packet filters.
For an excellent and detailed description on how to create a DMZ with Proxy Server 2.0, go to the Resoruces page to check out PSS Article ID Q191146 via Microsoft® TechNet.
How to determine the need for Screened Subnets
You will determine the number of screened subnets in a Proxy Server solution based on the security requirements of the organization you are administering. In fact, you will specify a screened subnet for each security requirement. That is, you should first find out which users or applications need access to the resources on the screened subnet. For example, to isolate resources that need to be accessed by all Internet-based users, users in a partner organization, and users within the private network, you would define three screened subnets.
Question: How do you determine the number of screened subnets in a Proxy Server solution?
Answer: You determine the security requirements of your organization.
Question: How do you determine the number of screened subnets in a Proxy Server solution?
Answer: You determine the security requirements of your organization.
Multiple interfaces or multiple servers?
You can define multiple screened subnets in a variety of ways:
The following table lists the methods for establishing multiple screened subnets, along with the reasons for selecting the different methods.
- By using multiple private network interfaces in a Proxy Server
- By using multiple proxy servers with a single interface
- By using a combination of both
The following table lists the methods for establishing multiple screened subnets, along with the reasons for selecting the different methods.
| You should select: | If the: |
| Multiple interfaces | System resources of the proxy server are not saturated Organization requires a centralized administration model |
| Multiple servers | Performance for the screened subnet needs to be maximized Organization requires a decentralized administration model |
Creating a Hierarchy
In designs that require more than one screened subnet created by multiple proxy servers, you place the proxy servers in a hierarchy.
This will enable you to delegate the administration of the screened subnets effectively. Once you have decided to create a hierarchy, you should design it as follows:
In the next lesson, you will learn how to ensure a secure network by using Proxy Server packet filters.
- Specify broad security requirements at the top of the hierarchy, such as the security requirements for an entire organization
- Specify stronger security requirements lower in the hierarchy, such as the security requirements for a department or application
In the next lesson, you will learn how to ensure a secure network by using Proxy Server packet filters.