| Lesson 2 | Restricting access to Internet resources |
| Objective | Describe the method used to restrict access to Internet resources. |
Restricting Access to Internet Resources
Proxy Server 2.0 can be used to restrict types of Internet access for internal network users. You can set access controls to limit access to a number of network protocols and services. For example, you might want to limit access to AOL to a small group of executives that refuse to learn how to use their computers. In this case, you would configure the WinSock Proxy service to limit access to the AOL protocol to only the members of the group to which these executives belong. This brings up an important point regarding access control functionality in Proxy Server 2.0. You can only configure granular permissions for individual application protocols, and not for content.
For example, you might wish to restrict access to specific, approved Web sites to the temp workers group, but allow unfettered access to all other users in the organization. You cannot do this in Proxy Server 2.0 because domain and cache filters are applied to everyone accessing Internet resources via the Proxy Server, and not just to selected users or groups.
How you restrict access will depend on whether the network you are administering is based on Active Directory (tm) or not. The following series of images SlideShow below gives you instructions for how to restrict access in both situations.
How you restrict access will depend on whether the network you are administering is based on Active Directory (tm) or not. The following series of images SlideShow below gives you instructions for how to restrict access in both situations.

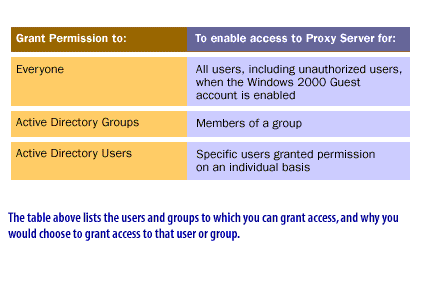

Grant Permission to
| Grant Permission to: | To enable access to Proxy Server for: |
| Everyone | All users, including unauthorized users, when the Windows 2000 Guest account is enabled |
| Active Directory Groups | Members of a group |
| Active Directory Users | Specific users granted permission on an individual basis |
If your network design consists mostly of other operating systems, or your design will not include Active Directory, you can specify that Proxy Server be installed on a standalone Windows (r)2000-based server. The standalone server has local users and groups that you can use to grant Proxy Server access.
Networks not based on Active Directory
If the network consists of other operating systems, you can specify that the other operating systems replicate the user accounts to the Windows 2000-based computer running Proxy Server. For example, in a network that is based on Novell Directory Services (NDS), you would specify that NDS users and groups be replicated to the proxy server by using Novell software.
You can also specify that the Guest account on the proxy server be enabled and granted Proxy Server access, thereby allowing anonymous access to the proxy server. Finally, you can specify that the "Everyone" group have access. The Everyone group includes the Guest account and even unauthenticated users. By allowing access to the Everyone group, you eliminate your ability to exercise any access controls over what internal network users can access over the Internet. In the next lesson, you will learn which factors to consider when determining the number of screened subnets required in the Internet connectivity design.
You can also specify that the Guest account on the proxy server be enabled and granted Proxy Server access, thereby allowing anonymous access to the proxy server. Finally, you can specify that the "Everyone" group have access. The Everyone group includes the Guest account and even unauthenticated users. By allowing access to the Everyone group, you eliminate your ability to exercise any access controls over what internal network users can access over the Internet. In the next lesson, you will learn which factors to consider when determining the number of screened subnets required in the Internet connectivity design.