Proxy servers used at the edge of a Private Network
Proxy servers are often used at the edge of a private network to provide an additional layer of security and control for outbound internet traffic. When used in this way, a proxy server sits between the private network and the public internet, and acts as an intermediary between client devices on the private network and external servers on the internet.
The primary benefit of using a proxy server at the edge of a private network is that it allows for fine-grained control over outbound internet traffic. This can help prevent security breaches and data leaks by blocking access to known malicious websites or restricting access to sensitive resources or applications. In addition, proxy servers can provide caching and bandwidth optimization features that can help improve the performance and efficiency of outbound internet traffic. By caching frequently accessed content, a proxy server can reduce the amount of bandwidth required to access external resources, which can help improve network performance and reduce costs.
Another benefit of using a proxy server at the edge of a private network is that it can provide an additional layer of anonymity and privacy for outbound internet traffic. By acting as an intermediary between the private network and external servers, a proxy server can mask the IP address and other identifying information of the client devices on the private network, which can help protect privacy and confidentiality. Overall, using a proxy server at the edge of a private network can provide numerous benefits in terms of security, control, performance, and privacy for outbound internet traffic. However, it's important to configure and manage the proxy server carefully to ensure that it meets the requirements of the organization and does not introduce any additional security or performance issues.
Another benefit of using a proxy server at the edge of a private network is that it can provide an additional layer of anonymity and privacy for outbound internet traffic. By acting as an intermediary between the private network and external servers, a proxy server can mask the IP address and other identifying information of the client devices on the private network, which can help protect privacy and confidentiality. Overall, using a proxy server at the edge of a private network can provide numerous benefits in terms of security, control, performance, and privacy for outbound internet traffic. However, it's important to configure and manage the proxy server carefully to ensure that it meets the requirements of the organization and does not introduce any additional security or performance issues.
Proxy Server within or at the edge of the Private Network
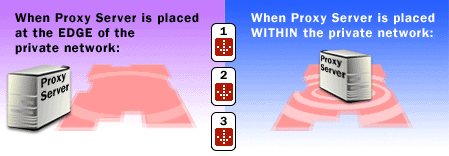

Web object are cached for network segments within an organization to reduce private network traffic.
3) Web objects are cached for the entire organization.
Screened subnets are created within the private network, thereby protecting confidential data.
Screened subnets are created within the private network, thereby protecting confidential data.