| Lesson 8 | Determining Proxy Server Client Requirements |
| Objective | Identify the Proxy Server Client Requirements to be included in the Proxy Server Design |
Determining Proxy Server Client Requirements
When determining "proxy server client requirements" for using Internet Information Services (IIS) Proxy functionality, you should consider several factors that ensure compatibility, security, and performance. Here's how you can approach it:
Example: PAC File for Automatic Proxy Configuration
If you are using a PAC file to automatically configure proxy settings for clients, it might look like this:
This PAC file directs clients to use a proxy server (`proxyserver.example.com`) for all traffic except local addresses (`10.0.0.0` network).
Conclusion: To determine proxy server client requirements when using IIS Proxy functionality, focus on understanding the client systems and applications, configuring necessary network and security settings, and ensuring compatibility with authentication mechanisms and proxy configurations (manual or automatic). Proper testing and monitoring are crucial to ensure that the proxy functions correctly for all clients.
You must determine the proxy server client requirements in order to specify private network address ranges and select appropriate software for connecting to the proxy server. Understanding client requirements helps ensure the proxy configuration (such as address ranges for internal networks and appropriate software settings) will work as expected for all clients. Properly defining these elements is essential to ensure seamless communication between clients and the proxy server, particularly in managing access control, security, and network traffic.
- Identify Client Types and Versions:
- Client Browser/Software Support: Ensure that the client systems (browsers, apps, etc.) support proxy configurations. Some older browsers or applications may not handle proxies efficiently.
- Authentication Requirements: If the proxy server uses authentication, ensure that client software supports the type of authentication (e.g., Basic, NTLM, Kerberos, etc.).
- Networking Requirements:
- HTTP/HTTPS Support: Ensure that the clients can support both HTTP and HTTPS traffic through the proxy. HTTPS traffic may require special configurations like SSL offloading or passthrough, depending on the security settings.
- Proxy Bypass for Local Traffic: Determine if there is a need for bypassing the proxy for local addresses. This is especially relevant for internal network access.
- Ports: Ensure that clients have the necessary ports open to communicate with the IIS proxy (default ports include 80 for HTTP and 443 for HTTPS).
- Proxy Configuration on Client Side:
- Manual or Automatic Configuration: Clients can either have proxies manually configured (via browser settings or system-wide) or automatically configured through technologies like Proxy Auto-Configuration (PAC) files or Web Proxy Auto-Discovery Protocol (WPAD).
- PAC Files: If you are using PAC files to automatically configure proxy settings, ensure the clients are configured to use these correctly.
- Group Policy for Windows Clients: If using Windows-based clients, you can manage proxy settings using Group Policy (GPO). This can enforce uniform settings across an organization.
- Authentication Mechanisms:
- Anonymous Access: If using anonymous access for public-facing services, ensure that clients don't require specific authentication methods.
- Basic or Integrated Authentication: If authentication is required, make sure the clients support it. For example, older or custom-built applications may not support modern authentication schemes.
- Bandwidth and Performance Considerations
- Caching: Proxy servers often cache resources to improve performance for clients. Ensure clients can benefit from caching based on the type of content served (e.g., static files, images, etc.).
- Load Balancing: If you're using load balancing in conjunction with IIS proxying, verify that clients can handle redirects or sessions properly when servers switch.
- Security Considerations:
- SSL/TLS Configuration: Clients must be configured to handle secure connections properly. This includes supporting the necessary TLS versions and ciphers.
- Client Certificates: If the proxy requires client certificates for authentication, ensure that clients can manage and present the certificates appropriately.
- Firewall Settings: Check that the client's firewall allows outgoing traffic on the required ports for the proxy server.
- Logging and Monitoring: Proxy Logs: Make sure the client interaction with the proxy is logged properly for auditing and troubleshooting purposes. The IIS logs can help in diagnosing proxy-related issues.
- Testing and Validation:
- Testing Proxy Settings: Once the proxy configuration is in place, test it with various client types (browsers, mobile apps, etc.) to ensure that all the traffic passes through the proxy correctly.
- Monitoring Client Feedback: After deployment, monitor feedback from users to ensure there are no issues with client connectivity through the proxy server.
Example: PAC File for Automatic Proxy Configuration
If you are using a PAC file to automatically configure proxy settings for clients, it might look like this:
function FindProxyForURL(url, host) {
// Bypass proxy for local addresses
if (isInNet(host, "10.0.0.0", "255.255.255.0")) {
return "DIRECT";
}
// Use proxy for all other traffic
return "PROXY proxyserver.example.com:8080";
}
This PAC file directs clients to use a proxy server (`proxyserver.example.com`) for all traffic except local addresses (`10.0.0.0` network).
Conclusion: To determine proxy server client requirements when using IIS Proxy functionality, focus on understanding the client systems and applications, configuring necessary network and security settings, and ensuring compatibility with authentication mechanisms and proxy configurations (manual or automatic). Proper testing and monitoring are crucial to ensure that the proxy functions correctly for all clients.
You must determine the proxy server client requirements in order to specify private network address ranges and select appropriate software for connecting to the proxy server. Understanding client requirements helps ensure the proxy configuration (such as address ranges for internal networks and appropriate software settings) will work as expected for all clients. Properly defining these elements is essential to ensure seamless communication between clients and the proxy server, particularly in managing access control, security, and network traffic.
- Specifying private network IP Address Ranges:
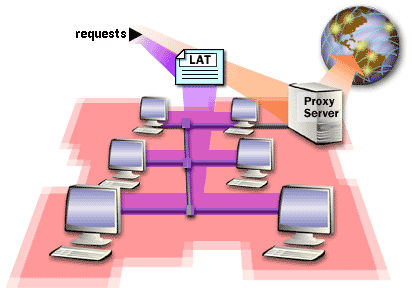
You must identify the IP address ranges within the private network so that you can specify these address ranges in the Proxy Server design. Proxy Server clients can then determine if the destination IP address in an IP packet must be sent directly to the private network destination or forwarded to the proxy server. The IP address ranges that you specify are stored in the local address table (LAT) file on the proxy server. When requests are sent to the proxy server, the proxy server uses the LAT to determine if the request is within the private network or on the Internet. The following series of images describes computers on a privateNetwork with and without a proxy Server Client.
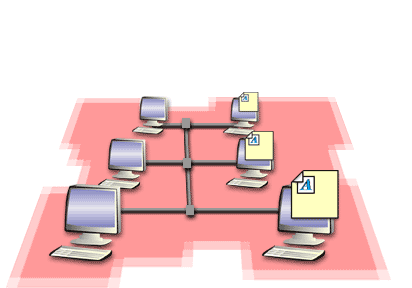
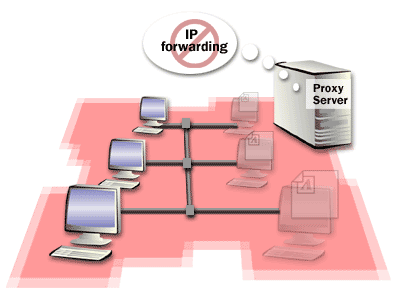
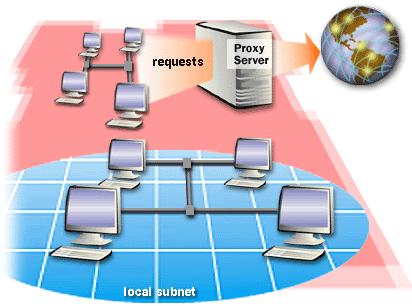
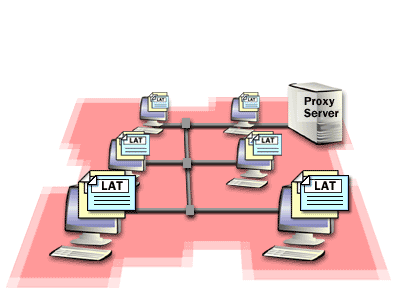
- Specify Private Network IP Address Ranges
- Select Software for Connecting to Proxy Server
You determine the Proxy Server client requirements so that you can specify the private network address ranges and select the appropriate software for connecting to Proxy Server.
- You must identify the IP address ranges within the private network so that you can specify these address ranges in the Proxy Server design. Proxy Server clients can then determine if the destination IP address in an IP packet must be sent directly to the private network destination, or forwarded to the proxy server.
- The IP address ranges that you specify are stored in the local address table (LAT) file on the proxy server. When requests are sent to the proxy server, the proxy server uses the LAT to determine if the request is within the private network or on the Internet.
Specifying Private Network IP Address Ranges
- For computers on the private network that do not have Proxy Server client software, you need to specify the IP address of the proxy server's private network interface as the default gateway. Because the proxy server is the default gateway for the computer, all requests that are not on the computer's local subnet are forwarded to the proxy server. The proxy server forwards the request to the Internet.
- When the computers on the private network have Proxy Server client software installed, they have a local copy of the LAT file. The Proxy Server clients use their local copy of the LAT file to determine if requests are within the private network, or on the Internet. Private network requests are sent directly to the destination within the private network. Internet requests are sent to the proxy server.
Computers On a private network with or without Proxy Server Client.
Selecting Software for connection to Proxy Server
You can specify that the private network interface of the proxy server is the default gateway entry for computers on the private network.
If you specify the proxy server as the default gateway, the private network traffic increases because all traffic destined for other subnets in the private network is forwarded first to the proxy server and then on to the final destination. In order to prevent this, specify that the private network computers be configured with software to forward traffic to the proxy server if the final destination is the Internet.
The following table lists the software options for private network computers and the reason to include the options in your design.
If you specify the proxy server as the default gateway, the private network traffic increases because all traffic destined for other subnets in the private network is forwarded first to the proxy server and then on to the final destination. In order to prevent this, specify that the private network computers be configured with software to forward traffic to the proxy server if the final destination is the Internet.
The following table lists the software options for private network computers and the reason to include the options in your design.
| Select: | If you need to support: |
| Microsoft® Internet Explorer 10.0 | HTTP and FTP traffic only Any operating system that includes Internet Explorer 5.0 Packet filters and domain filters for filtering traffic |
| Proxy Server client | All IP protocol traffic Any operating system that supports the WinSock standard Packet filters and domain filters for filtering traffic IPX/SPX-based private networks |
| SOCKS | All IP protocols supported by the SOCKS applications UNIX, Macintosh, or operating systems that run SOCKS-compatible applications SOCKS rules, protocol rules, and IP-packet filters for filtering traffic |
| No client software | All IP protocols Any operating system with the default gateway configured to send Internet traffic to the proxy server Protocol rules, and IP-packet filters for filtering traffic |
Question: When a computer on the private network does not have Proxy Server Client software, what do you need to specify as the default gateway?
Answer:The IP address of the proxy server's private network interface
The next lesson wraps-up this module.
Answer:The IP address of the proxy server's private network interface
The next lesson wraps-up this module.