| Lesson 2 | Restricting Internet traffic using IP Filters |
| Objective | Describe how IP filters enhance NAT Security |
Restricting Internet Traffic using IP Filters
Restrict Access
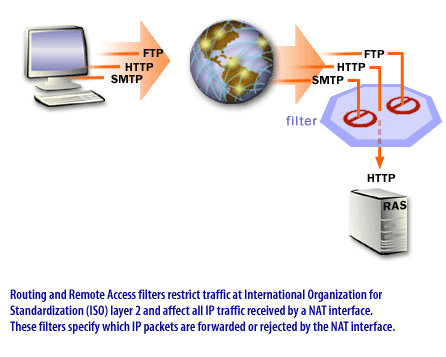
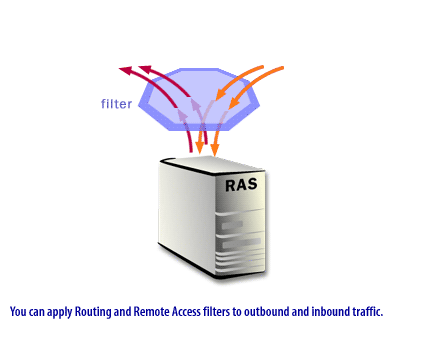
To restrict access to the Internet or the private network, you can specify unique Routing and Remote Access IP filters for each NAT interface.
These filters are based on an incoming or outgoing IP address range and protocol.
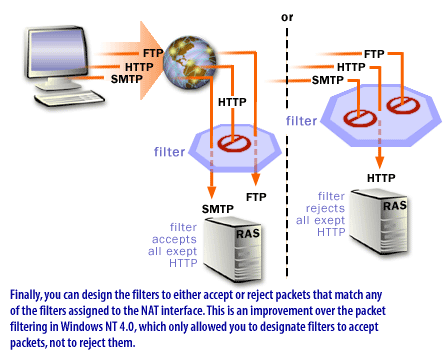
For example, if you wanted to prevent internal network users from using FTP resources on the Internet, you could place a filter on outbound packets so that any request for an FTP resource at a particular site would be dropped.
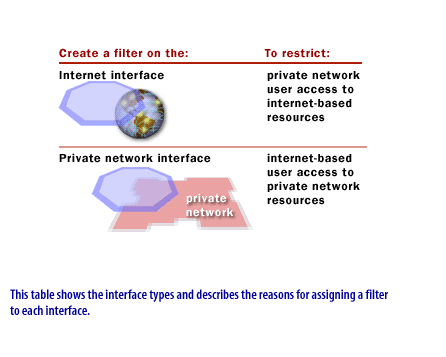
You can specify Routing and Remote Access IP filters to restrict:
The following series of images illustrates the benefits of using IP filters to restrict Internet traffic.
These filters are based on an incoming or outgoing IP address range and protocol.
For example, if you wanted to prevent internal network users from using FTP resources on the Internet, you could place a filter on outbound packets so that any request for an FTP resource at a particular site would be dropped.
You can specify Routing and Remote Access IP filters to restrict:
- Internet-based user access to private network resources
- Private network user access to Internet-based resources, such as partner networks or central offices
The following series of images illustrates the benefits of using IP filters to restrict Internet traffic.
Using IP Filters
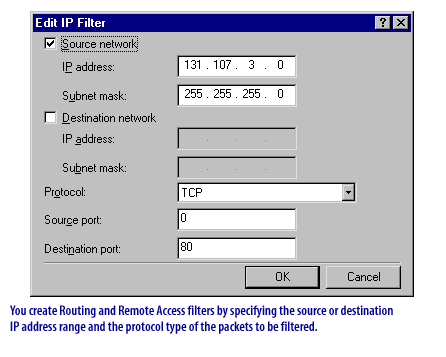
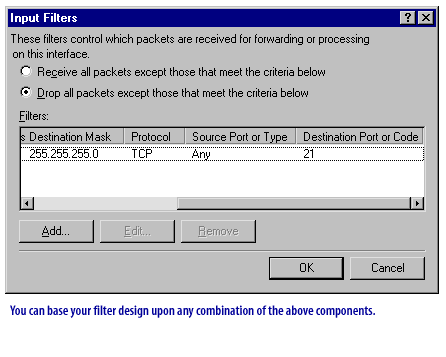
Question: How are Routing and Remote Access filters created?
Answer: By specifying the source or destination IP address range and the protocol type of the packets to be filtered.
Packet filtering is a very difficult way to implement outbound security.
In the next lesson you will learn how to allow access to specific computers and applications using address pools and special ports.
Answer: By specifying the source or destination IP address range and the protocol type of the packets to be filtered.
Packet filtering is a very difficult way to implement outbound security.
Disadvantages of Packet Filtering
You must specify the destination IP address and the protocol type for each filtered connection. You can filter for a specific host or network ID, or you can block all traffic of a particular type.
If you want to perform any level of granular control over a group of sites you wish to block, it can become a very complex and time-consuming affair. It is better to use Proxy Server if you require this type of functionality.
Routing and Remote Access IP filters provide similar security to firewall filters, which can protect your network from incoming packets. Again, the level of complexity required in such a filtering scheme might be overwhelming to an inexperienced administrator or a SOHO (small office/home office) user.
Packet filtering firewalls are part of a router which work at the network level of the OSI model or the IP layer of TCP/IP. In this firewall every packet is compared to a set of criteria prior to forwarding it. The firewall can drop the packet; forward the packet to originator depending on the packet and the criteria. The advantage of packet filter firewall is "low cost and low impact on network performance".
Routing and Remote Access IP filters provide similar security to firewall filters, which can protect your network from incoming packets. Again, the level of complexity required in such a filtering scheme might be overwhelming to an inexperienced administrator or a SOHO (small office/home office) user.
Packet filtering firewalls are part of a router which work at the network level of the OSI model or the IP layer of TCP/IP. In this firewall every packet is compared to a set of criteria prior to forwarding it. The firewall can drop the packet; forward the packet to originator depending on the packet and the criteria. The advantage of packet filter firewall is "low cost and low impact on network performance".
Current filtering Tools are not Perfect
Despite the widespread availability of packet filtering in various hardware and software packages, packet filtering is still not a perfect tool.
The packet filtering capabilities of many of these products share, to a greater or lesser degree, common limitations:
- The packet filtering rules tend to be hard to configure. Although there is a range of difficulty, it mostly runs from slightly mind-twisting to brain-numbingly impossible.
- Once configured, the packet filtering rules tend to be hard to test.
- The packet filtering capabilities of many of the products are incomplete, making implementation of certain types of highly desirable filters difficult or impossible.
- Like anything else, packet filtering packages may have bugs in them; these bugs are more likely than proxying bugs to result in security problems. Usually, a proxy that fails simply stops passing data, while a failed packet filtering implementation may allow packets it should have denied.
Some Protocols are not well suited to Packet Filtering
Even with perfect packet filtering implementations, you will find that some protocols just are not well suited to security via packet filtering, for reasons we'll discuss later in this book. Such protocols include the Berkeley "r" commands (rcp, rlogin, rdist, rsh, etc.) and RPC-based protocols such as NFS and NIS/YP.
(The problems of using packet filtering to deal with these protocols are discussed in Configuring Internet Services.)
Some policies cannot readily be enforced by normal packet filtering routers
The information that a packet filtering router has available to it does not allow you to specify some rules you might like to have. For example, packets say what host they come from, but generally not what user. Therefore, you cannot enforce restrictions on particular users. Similarly, packets say what port they are going to, but not what application; when you enforce restrictions on higher-level protocols, you do it by port number, hoping that nothing else is running on the port assigned to that protocol. Malicious insiders can easily subvert this kind of control.
In the next lesson you will learn how to allow access to specific computers and applications using address pools and special ports.